Service management. Firmware version 1.13.0
DHCP server configuration
Integrated DHCP server of the router allows you to configure LAN device network settings. Router DHCP server is able to send additional options to network devices, for example:
- default-router – IP address of the router used as default gateway;
- domain-name – domain name which will be used by client while solving host names via domain name system (DNS);
- dns-server – list of domain name server addresses for the current network that should be known by the client. Server addresses are listed in descending order of their preference.
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Enable IPv4/IPv6 DHCP server. | esr(config)# ip dhcp-server [vrf <VRF>] | <VRF> – VRF instance name, set by the string of up to 31 characters, within which the NTP server will operate. Set by the string of up to 31 characters. |
esr(config)# ipv6 dhcp-server [vrf <VRF>] | |||
2 | Set the DSCP code value for the use in IP headers of DHCP server egress packets (optionally). | esr(config)# ip dhcp-server dscp <DSCP> | <DSCP> – DSCP code value, takes values in the range of [0..63]. Default value: 61. |
3 | Create pool of DHCP server IPv4/IPv6 addresses and switch to its configuration mode. | esr(config)# ip dhcp-server pool <NAME> [vrf <VRF>] | <NAME> – IPv4/IPv6 server profile name, set by the string of up to 31 characters. <VRF> – VRF instance name, within which the NTP server will operate. Set by the string of up to 31 characters. |
esr(config)# ipv6 dhcp-server pool <NAME> [vrf <VRF>] | |||
4 | Specify IPv4/IPv6 address and mask for the subnet from which IPv4/IPv6 addresses pool will be allocated. | esr(config-dhcp-server)# network <ADDR/LEN> | <ADDR/LEN> – IP address and prefix of a subnet, defined as AAA.BBB.CCC.DDD/EE where each part AAA-DDD takes values of [0..255] and EE takes values of [1..32]. |
esr(config-ipv6-dhcp-server)# network <IPV6-ADDR/LEN> | <IPV6-ADDR/LEN> – IP address and prefix of a subnet, defined as X:X:X:X::X/EE where each X part takes values in hexadecimal format [0..FFFF] and EE takes values of [1..128]. | ||
5 | Add IPv4/IPv6 addresses range to the address pool of configurable DHCP server. | esr(config-dhcp-server)# address-range <FROM-ADDR>-<TO-ADDR> | <FROM-ADDR> – range starting IP address; <TO-ADDR> – range ending IP address; The addresses are defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. You can specify up to 32 IP addresses separated by commas. |
esr(config-ipv6-dhcp-server)# address-range <FROM-ADDR>-<TO-ADDR> | <FROM-ADDR> – range starting IP address; <TO-ADDR> – range ending IP address; The addresses are defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]. | ||
6 | Add IPv4/IPv6 address for a specific physical address to the address pool of configurable DHCP server (optionally). | esr(config-dhcp-server)# address <ADDR> | <ADDR> – client IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]; <MAC> – MAC address of the client, which will be given the IP address, is defined as XX: XX: XX: XX: XX: XX where each part takes the values of [00..FF]. <CI> – client identifier according to DHCPOption61. Can be specified as follows:
|
esr(config-ipv6-dhcp-server)# address <ADDR> mac-address <MAC> | <IPV6-ADDR> – client IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]; <MAC> – MAC address of the client, which will be given the IP address, defined as XX: XX: XX: XX: XX: XX where each part takes the values of [00..FF]. | ||
7 | Specify the list of default gateway IPv4 addresses which will be transmitted by DHCP server to clients through DHCP option 3. | esr(config-dhcp-server)# default-router <ADDR> | <ADDR> – default gateway IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]; You can specify up to 8 IP addresses separated by commas. |
8 | Specify network domain DNS name. Domain name is transmitted to clients as part of DHCP option 15 (optionally). | esr(config-dhcp-server)# domain-name <NAME> | <NAME> – router domain name, set by the string from 1 to 255 characters. |
esr(config-ipv6-dhcp-server)# domain-name <NAME> | |||
9 | Specify DNS server IPv4/IPv6 addresses list. The list is transmitted to clients as part of DHCP option 6 (optionally). | esr(config-dhcp-server)# dns-server <ADDR> | <ADDR> – DNS server IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. You can specify up to 8 IP addresses separated by commas. |
esr(config-ipv6-dhcp-server)# dns-server <IPV6-ADDR> | <IPV6-ADDR> – DNS server IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]. You can specify up to 8 IP addresses separated by commas. | ||
10 | Specify maximum IP addresses lease time (optionally). If DHCP client requests the lease time that exceeds a maximum value, the time specified by the command will be set. | esr(config-dhcp-server)# max-lease-time <TIME> | <TIME> – maximal IP address lease time, sets in format DD:HH:MM, where:
Default value: 1 day |
esr(config-ipv6-dhcp-server)# max-lease-time <TIME> | |||
11 | Specify the lease time for which a client will be given IP address (optionally). This time will be used if a client did not request the certain lease time. | esr(config-dhcp-server)# default-lease-time <TIME> | <TIME> – maximal IP address lease time, sets in format DD:HH:MM, where:
Default value: 12 hours. |
esr(config-ipv6-dhcp-server)# default-lease-time <TIME> | |||
12 | Create supplier class identifier (DHCP Option 60) (optionally). | esr(config)# ip dhcp-server vendor-class-id <NAME> | <NAME> – carrier class identifier, set by the string of up to 31 characters. |
esr(config)# ipv6 dhcp-server vendor-class-id <NAME> | |||
13 | Specify specific supplier information (DHCP Option 43). | esr(config-dhcp-vendor-id)# vendor-specific-options <HEX> | <HEX> – vendor-specific information, specified in hexadecimal format up to 128 symbols. |
esr(config-ipv6-dhcp-vendor-id)# vendor-specific-options <HEX> | |||
14 | Specify NetBIOS server IP address (DHCP option 44) (optionally). | esr(config-dhcp-server)# netbios-name-server <ADDR> | <ADDR> – NetBIOS server IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. You can set up to 4 IP addresses. |
15 | Specify tftp server IP address (DHCP option 150) (optionally). | esr(config-dhcp-server)# tftp-server <ADDR> | <ADDR> – DNS server IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
Configuration example
Objective:
Configure DHCP server operation in a local network that belongs to the 'trusted' security zone. Specify IP address pool from 192.168.1.0/24 subnet for distribution to clients. Specify address lease time equal to 1 day. Configure transmission of the default route, domain name and DNS server addresses to clients using DHCP options.
Solution:
Create «trusted» security zone and determine the inherence of the network interfaces being used to zones:
esr# configure
esr(config)# security zone trusted
esr(config-zone)# exitCreate address pool named «Simple» and add IP address range intended for server clients lease into this pool. Specify parameters of the subnet that the pool belongs to, and the lease time for addresses:
esr# configure
esr(config)# ip dhcp-server pool Simple
esr(config-dhcp-server)# network 192.168.1.0/24
esr(config-dhcp-server)# address-range 192.168.1.100-192.168.1.125
esr(config-dhcp-server)# default-lease-time 1:00:00Configure transfer of additional network parameters to clients:
- default route: 192.168.1.1;
- domain name: eltex.loc;
- DNS server list: DNS1: 172.16.0.1, DNS2: 8.8.8.8.
esr(config-dhcp-server)# domain-name "eltex.loc"
esr(config-dhcp-server)# default-router 192.168.1.1
esr(config-dhcp-server)# dns-server 172.16.0.1,8.8.8.8
esr(config-dhcp-server)# exitTo enable IP address distribution from the configurable pool by DHCP server, IP interface should be created on the router that belongs to the same subnet as the pool addresses.
esr(config)# interface gigabitethernet 1/0/1
esr(config-if-gi)# security-zone trusted
esr(config-if-gi)# ip address 192.168.1.1/24
esr(config-if-gi)# exitTo enable DHCP message transmission to the server, you should create the respective port profiles including source port 68 and destination port 67 used by DHCP and create the allowing rule in the security policy for UDP packet transmission:
esr(config)# object-group service dhcp_server
esr(config-object-group-service)# port-range 67
esr(config-object-group-service)# exit
esr(config)# object-group service dhcp_client
esr(config-object-group-service)# port-range 68
esr(config-object-group-service)# exit
esr(config)# security zone-pair trusted self
esr(config-zone-pair)# rule 30
esr(config-zone-rule)# match protocol udp
esr(config-zone-rule)# match source-port dhcp_client
esr(config-zone-rule)# match destination-port dhcp_server
esr(config-zone-rule)# action permit
esr(config-zone-rule)# enable
esr(config-zone-rule)# exit
esr(config-zone-pair)# exitEnable server operation:
esr(config)# ip dhcp-server
esr(config)# exitTo view the list of leased addresses, use the following command:
esr# show ip dhcp binding To view the configured address pools, use the following commands:
esr# show ip dhcp server pool
esr# show ip dhcp server pool SimpleConfiguration of settings for IPv6 is performed by analogy to IPv4.
Destination NAT configuration
Destination NAT (DNAT) function includes destination IP address translation for packets transferred through the network gateway.
DNAT is used for redirection of traffic, coming to a specific 'virtual' address in a public network, to a 'real' server in LAN located behind the network gateway. This function may be used for establishing a public access to servers located within the private network without any public network address.
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Switch to the configuration mode of destination address translation service. | esr(config)# nat destination | |
2 | Create a pool of IP addresses and/or TCP/UDP ports with a specific name (optionally). | esr(config-dnat)# pool <NAME> | <NAME> – NAT addresses pool name, set by the string of up to 31 characters. |
3 | Set the internal IP address which will replace a destination IP address. | esr(config-dnat-pool)# ip address <ADDR> | <ADDR> – IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
4 | Set the internal TCP/UDP port which will replace a destination TCP/UDP port. | esr(config-dnat-pool)# ip port <PORT> | <PORT> – TCP/UDP port, takes values of [1..65535]. |
5 | Create a rule group with a specific name. | esr(config-dnat)# ruleset <NAME> | <NAME> – rule group name, set by the string of up to 31 characters. |
6 | Specify VRF instance, in which the given rule group will operate (optionally). | esr(config-dnat-ruleset)# ip vrf forwarding <VRF> | <VRF> – VRF name, set by the string of up to 31 characters. |
7 | Set the rule group scope. The rules will be applied only to traffic coming from a certain zone or interface. | esr(config-dnat-ruleset)# from { zone <NAME> | <NAME> – isolation zone name; <IF> – device interface name; <TUN> – device tunnel name; default – denotes a group of rules for all traffic, the source of which did not fall under the criteria of other groups of rules. |
8 | Specify a rule with a certain number. The rules are proceeded in ascending order. | esr(config-dnat-ruleset)# rule <ORDER> | <ORDER> – rule number, takes values of [1..10000]. |
9 | Specify the profile of IP addresses {sender | recipient} for which the rule should work. | esr(config-dnat-rule)# match [not] | <OBJ-GROUP-NETWORK-NAME> – IP addresses profile name, set by the string of up to 31 characters. “Any” value points at any source IP address. |
10 | Specify the profile of services (tcp/udp ports) {sender | recipient} for which the rule should work (optionally). | esr(config-dnat-rule)# match [not] | <PORT-SET-NAME> – port profile name, set by the string of up to 31 characters. “Any” value points at any source TCP/UDP port. |
11 | Set name or number of IP for which the rule should work (optional). | esr(config-dnat-rule)# match [not] | <TYPE> – protocol type, takes the following values: esp, icmp, ah, eigrp, ospf, igmp, ipip, tcp, pim, udp, vrrp, rdp, l2tp, gre. “Any” value points at any protocol type. <ID> – IP identification number, takes values of [0x00-0xFF]. |
12 | Specify the type and code of ICMP messages for which the rule should work (if ICMP is selected as protocol) (optionally). | esr(config-dnat-rule)# match [not] | <ICMP_TYPE> – ICMP message type, takes values of [0..255]. <ICMP_CODE> – ICMP message code, takes values of [0..255]. “Any” value points at any message code. <TYPE-NAME> – ICMP message type name. |
13 | Specify the action “translation of source address and port” for the traffic meeting the requirements of “match” commands. | esr(config-dnat-rule)# action destination-nat | off – translation is disabled; pool<NAME> – name of the pool that contains IP addresses and/or TCP/UDP ports set; netmap <ADDR/LEN> – subnet IP address and mask used during translation. The parameter is defined as AAA.BBB.CCC.DDD/EE where each part AAA-DDD takes values of [0..255] and EE takes values of [1..32]. |
14 | Activate a configured rule. | esr(config-dnat-rule)# enable |
1 When using the not key, the rule will work for values which are not included in a specified profile
Each “match” command may contain “not” key. When using the key, packets that do not meet the given requirement will fall under the rule.
You can obtain more detail information about router configuration in “CLI command reference guide”.
Destination NAT configuration example
Objective:
Establish access from the public network, that belongs to the 'UNTRUST' zone, to LAN server in 'TRUST' zone. Server address in LAN – 10.1.1.100. Server should be accessible from outside the network–address 1.2.3.4, access port 80.
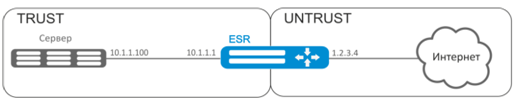
Solution:
Create 'UNTRUST' and 'TRUST' security zones. Specify the inherence of the network interfaces being used to zones. Assign IP ‑addresses to interfaces simultaneously.
esr# configure
esr(config)# security zone UNTRUST
esr(config-zone)# exit
esr(config)# security zone TRUST
esr(config-zone)# exit
esr(config)# interface gigabitethernet 1/0/1
esr(config-if-gi)# security-zone TRUST
esr(config-if-gi)# ip address 10.1.1.1/25
esr(config-if-gi)# exit
esr(config)# interface tengigabitethernet 1/0/1
esr(config-if-te)# ip address 1.2.3.4/29
esr(config-if-te)# security-zone UNTRUST
esr(config-if-te)# exitCreate IP address and port profiles required for configuration of the Firewall and DNAT rules.
- NET_UPLINK – public network address profile;
- SERVER_IP – local area network address profile;
- SRV_HTTP – port profile.
esr(config)# object-group network NET_UPLINK
esr(config-object-group-network)# ip address 1.2.3.4
esr(config-object-group-network)# exitesr(config)# object-group service SRV_HTTP
esr(config-object-group-service)# port 80
esr(config-object-group-service)# exitesr(config)# object-group network SERVER_IP
esr(config-object-group-network)# ip address 10.1.1.100
esr(config-object-group-network)# exitProceed to DNAT configuration mode and create destination address and port pool that will be used for translation of packet addresses coming to address 1.2.3.4 from the external network.
esr(config)# nat destination
esr(config-dnat)# pool SERVER_POOL
esr(config-dnat-pool)# ip address 10.1.1.100
esr(config-dnat-pool)# ip port 80
esr(config-dnat-pool)# exitCreate 'DNAT' rule set which will be used for address translation. In the set attributes, specify that the rules are applying only to packets coming from the 'UNTRUST' zone. Rule set includes data matching requirements for destination address and port (match destination-address, match destination-port) and for the protocol. Also, the set includes an action that applies to the data that satisfy all of the rules (action destination-nat). The rule set is applied with 'enable' command.
esr(config-dnat)# ruleset DNAT
esr(config-dnat-ruleset)# from zone UNTRUST
esr(config-dnat-ruleset)# rule 1
esr(config-dnat-rule)# match destination-address NET_UPLINK
esr(config-dnat-rule)# match protocol tcp
esr(config-dnat-rule)# match destination-port SRV_HTTP
esr(config-dnat-rule)# action destination-nat pool SERVER_POOL
esr(config-dnat-rule)# enable
esr(config-dnat-rule)# exit
esr(config-dnat-ruleset)# exit
esr(config-dnat)# exitTo transfer the traffic coming from 'UNTRUST' zone into 'TRUST' zone, create the respective pair of zones. Only DNAT-translated traffic with the destination address matching the 'SERVER_IP' specified in the profile should be transferred.
esr(config)# security zone-pair UNTRUST TRUST
esr(config-zone-pair)# rule 1
esr(config-zone-pair-rule)# match destination-address SERVER_IP
esr(config-zone-pair-rule)# match destination-nat
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# enable
esr(config-zone-pair-rule)# exit
esr(config-zone-pair)# exit
esr(config)# exitConfiguration changes will take effect when the configuration is applied:
esr# show ip nat destination pools
esr# show ip nat destination rulesets
esr# show ip nat proxy-arp
esr# show ip nat translationsSource NAT configuration
Source NAT (SNAT) function substitutes source address for packets transferred through the network gateway. When packets are transferred from LAN into public network, source address is substituted to one of the gateway public addresses. Additionally, source port substitution may be added to the source address. When packets are transferred back from public network to LAN, address and port are reverted to their original values.
SNAT function enables Internet access for computers located in LAN. At that, there is no need in assigning public IP addresses for these computers.
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Switch to the configuration mode of source address translation service. | esr(config)# nat source | |
2 | Create a pool of IP addresses and/or TCP/UDP ports with a specific name (optionally). | esr(config-snat)# pool <NAME> | <NAME> – NAT addresses pool name, set by the string of up to 31 characters. |
3 | Set the range of IP addresses which will replace a source IP address. | esr(config-snat-pool)# ip address-range <IP>[-<ENDIP>] | <IP> – IP address of the beginning of the range, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]; <ENDIP> – IP address of the end of the range, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. If IP address of the end of the range is not specified, only IP address of the beginning of the range is used as IP address for translation. |
4 | Specify the range of external TCP/UDP ports which will replace a source TCP/UDP port. | esr(config-snat-pool)# ip port-range <PORT>[-<ENDPORT>] | <PORT> – TCP/UDP port of the beginning of range, takes values of [1..65535]; <ENDPORT> – TCP/UDP port of the end of range, takes values of [1..65535]. If TCP/UDP port of the end of the range is not specified, only TCP/UDP port of the beginning of the range is used as TCP/UDP port for translation. |
5 | Set the internal TCP/UDP port which will replace a source TCP/UDP port. | esr(config-snat-pool)# ip port <PORT> | <PORT> – TCP/UDP port, takes values of [1..65535]. |
6 | Enable NAT persistent functions. | esr(config-snat-pool)# persistent | |
7 | Create a rule group with a specific name. | esr(config-snat)# ruleset <NAME> | <NAME> – rule group name, set by the string of up to 31 characters. |
8 | Specify VRF instance, in which the given rule group will operate (optionally). | esr(config-snat-ruleset)# ip vrf forwarding <VRF> | <VRF> – VRF name, set by the string of up to 31 characters. |
9 | Set the rule group scope. The rules will be applied only to traffic coming to a certain zone or interface. | esr(config-snat-ruleset)# to { zone <NAME> | | <NAME> – isolation zone name; <IF> – device interface name; <TUN> – device tunnel name |
10 | Specify a rule with a certain number. The rules are proceeded in ascending order. | esr(config-snat-ruleset)# rule <ORDER> | <ORDER> – rule number, takes values of [1..10000]. |
11 | Specify the profile of IP addresses {sender | recipient} for which the rule should work. | esr(config-snat-rule)# match [not] | <OBJ-GROUP-NETWORK-NAME> – IP addresses profile name, set by the string of up to 31 characters. “Any” value points at any source IP address. |
12 | Specify the profile of IP addresses {sender| recipient} for which the rule should work (optionally). | esr(config-snat-rule)# match [not] | <PORT-SET-NAME> – port profile name, set by the string of up to 31 characters. “Any” value points at any source TCP/UDP port. |
13 | Set name or number of IP for which the rule should work (optional). | esr(config-snat-rule)# match [not] | <TYPE> – protocol type, takes the following values: esp, icmp, ah, eigrp, ospf, igmp, ipip, tcp, pim, udp, vrrp, rdp, l2tp, gre. “Any” value points at any protocol type. <ID> – IP identification number, takes values of [0x00-0xFF]. |
14 | Specify the type and code of ICMP messages for which the rule should work (optionally). | esr(config-snat-rule)# match [not] | <ICMP_TYPE> – ICMP message type, takes values of [0..255]. <ICMP_CODE> – ICMP message code, takes values of [0..255]. “Any” value points at any message code. <TYPE-NAME> – ICMP message type name |
15 | Specify the action “translation of source address and port” for the traffic meeting the requirements of “match” command. | esr(config-snat-rule)# action source-nat { off | | off – translation is disabled; pool<NAME> – name of the pool that contains IP addresses and/or TCP/UDP ports set; netmap <ADDR/LEN> – subnet IP address and mask used during translation; static – option for static NAT organization. The parameter is defined as AAA.BBB.CCC.DDD/EE where each part AAA-DDD takes values of [0..255] and EE takes values of [1..32]. interface [FIRST_PORT – LAST_PORT] – specify the translation to the interface IP address. If the range of TCP/UDP ports is additionally specified, the translation will occur only for the sender TCP/UDP ports included in the specified range. |
16 | Activate a configured rule. | esr(config-snat-rule)# enable |
1 When using the not key, the rule will work for values which are not included in a specified profile
Each “match” command may contain “not” key. When using the key, packets that do not meet the given requirement will fall under the rule.
You can obtain more detail information about router configuration in “CLI command reference guide”.
Configuration example 1
Objective:
Configure access for users in LAN 10.1.2.0/24 to public network using Source NAT function. Specify public network address range for SNAT 100.0.0.100-100.0.0.249.
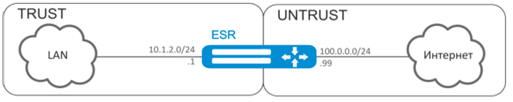
Solution:
Begin configuration with creation of security zones, configuration of network interfaces and their inherence to security zones. Create 'TRUST' zone for LAN and 'UNTRUST' zone for public network.
esr# configure
esr(config)# security zone UNTRUST
esr(config-zone)# exit
esr(config)# security zone TRUST
esr(config-zone)# exit
esr(config)# interface gigabitethernet 1/0/1
esr(config-if-gi)# ip address 10.1.2.1/24
esr(config-if-gi)# security-zone TRUST
esr(config-if-gi)# exit
esr(config)# interface tengigabitethernet 1/0/1
esr(config-if-te)# ip address 100.0.0.99/24
esr(config-if-te)# security-zone UNTRUST
esr(config-if-te)# exitFor SNAT function configuration and definition of rules for security zones, create 'LOCAL_NET' LAN address profile that includes addresses which are allowed to access the public network and 'PUBLIC_POOL' public network address profile.
esr(config)# object-group network LOCAL_NET
esr(config-object-group-network)# ip address-range 10.1.2.2-10.1.2.254
esr(config-object-group-network)# exit
esr(config)# object-group network PUBLIC_POOL
esr(config-object-group-network)# ip address-range 100.0.0.100-100.0.0.249
esr(config-object-group-network)# exitTo transfer traffic from 'TRUST' zone into 'UNTRUST' zone, create a pair of zones and add rules allowing traffic transfer in this direction. Additionally, there is a check in place to ensure that data source address belongs to 'LOCAL_NET' address range in order to limit the access to public network. Rules are applied with the enable command.
esr(config)# security zone-pair TRUST UNTRUST
esr(config-zone-pair)# rule 1
esr(config-zone-pair-rule)# match source-address LOCAL_NET
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# enable
esr(config-zone-pair-rule)# exit
esr(config-zone-pair)# exitConfigure SNAT service. First step is to create public network address pool for use with SNAT.
esr(config)# nat sourсe
esr(config-snat)# pool TRANSLATE_ADDRESS
esr(config-snat-pool)# ip address-range 100.0.0.100-100.0.0.249
esr(config-snat-pool)# exitSecond step is to create SNAT rule set. In the set attributes, specify that the rules are applying only to packets transferred to public network–into the 'UNTRUST' zone. Rules include a check which ensures that data source address belongs to 'LOCAL_NET' pool.
esr(config-snat)# ruleset SNAT
esr(config-snat-ruleset)# to zone UNTRUST
esr(config-snat-ruleset)# rule 1
esr(config-snat-rule)# match source-address LOCAL_NET
esr(config-snat-rule)# action source-nat pool TRANSLATE_ADDRESS
esr(config-snat-rule)# enable
esr(config-snat-rule)# exit
esr(config-snat-ruleset)# exitIn order the router could response to the ARP requests for addresses from the public pool, you should launch ARP Proxy service. ARP Proxy service is configured on the interface that IP address from 'PUBLIC_POOL' public network address profile subnet belongs to.
esr(config)# interface tengigabitethernet 1/0/1
esr(config-if-te)# ip nat proxy-arp PUBLIC_POOLTo enable public network access for LAN devices, they should be configured for routing–10.1.2.1 should be defined as a gateway address.
On the router, you should create the route for public network. Specify this route as a default using the following command.
esr(config)# ip route 0.0.0.0/0 100.0.0.1
esr(config)# exitConfiguration example 2
Objective:
Configure access for users in LAN 21.12.2.0/24 to public network using Source NAT function without the firewall. Public network address range for SNAT 200.10.0.100-200.10.0.249.

Solution:
Begin configuration with network interface configuration and disabling the firewall:
esr(config)# interface gigabitethernet 1/0/1
esr(config-if-gi)# ip address 21.12.2.1/24
esr(config-if-gi)# ip firewall disable
esr(config-if-gi)# exitesr(config)# interface tengigabitethernet 1/0/1
esr(config-if-te)# ip address 200.10.0.1/24
esr(config-if-te)# ip firewall disable
esr(config-if-te)# exitFor SNAT function configuration, create 'LOCAL_NET' LAN address profile that includes addresses which are allowed to access the public network and 'PUBLIC_POOL' public network address profile.
esr(config)# object-group network LOCAL_NET
esr(config-object-group-network)# ip address-range 21.12.2.2-21.12.2.254
esr(config-object-group-network)# exit
esr(config)# object-group network PUBLIC_POOL
esr(config-object-group-network)# ip address-range 200.10.0.100-200.10.0.249
esr(config-object-group-network)# exitConfigure SNAT service.
First step is to create public network address pool for use with SNAT:
esr(config)# nat source
esr(config-snat)# pool TRANSLATE_ADDRESS
esr(config-snat-pool)# ip address-range 200.10.0.100-200.10.0.249
esr(config-snat-pool)# exitSecond step is to create SNAT rule set. In the set attributes, specify that the rules are applying only to packets transferred to public network through te1/0/1 port. Rules include a check which ensures that data source address belongs to 'LOCAL_NET' pool:
esr(config-snat)# ruleset SNAT
esr(config-snat-ruleset)# to interface te1/0/1
esr(config-snat-ruleset)# rule 1
esr(config-snat-rule)# match source-address LOCAL_NET
esr(config-snat-rule)# action source-nat pool TRANSLATE_ADDRESS
esr(config-snat-rule)# enable
esr(config-snat-rule)# exit
esr(config-snat-ruleset)# exitIn order the router could response to the ARP requests for addresses from the public pool, you should launch ARP Proxy service. ARP Proxy service is configured on the interface that IP address from 'PUBLIC_POOL' public network address profile subnet belongs to:
esr(config)# interface tengigabitethernet 1/0/1
esr(config-if-te)# ip nat proxy-arp PUBLIC_POOLTo enable public network access for LAN devices, they should be configured for routing – 21.12.2.1 should be defined as a gateway address.
On the router, you should create the route for public network. Specify this route as a default using the following command:
esr(config)# ip route 0.0.0.0/0 200.10.0.254
esr(config)# exitStatic NAT configuration
Static NAT — static NAT sets a unique match between two addresses. In other words, when passing through the router the address is changed to another strictly specified one, one-to-one. The record about this translation is kept indefinitely until NAT reconfiguration is carried out on the router.
Configuration algorithm
Static NAT configuration is carried out by Source NAT means, the configuration algorithm is described in Section Source NAT configuration, configuration algorithm of the manual.
Static NAT configuration example
Objective:
Configure two-way and continuous translation from LAN for the addresses range of 21.12.2.100-21.12.2.150 to the public network 200.10.0.0/24. Public network address range for translation use – 200.10.0.100-200.10.0.150.

Solution:
Begin configuration with network interface configuration and disabling the firewall:
esr(config)# interface gigabitethernet 1/0/1
esr(config-if-gi)# ip address 21.12.2.1/24
esr(config-if-gi)# ip firewall disable
esr(config-if-gi)# exitesr(config)# interface tengigabitethernet 1/0/1
esr(config-if-te)# ip address 200.10.0.1/24
esr(config-if-te)# ip firewall disable
esr(config-if-te)# exitFor Static NAT configuration, create 'LOCAL_NET' LAN address profile, that includes local subnet, and 'PUBLIC_POOL' public network address profile.
esr(config)# object-group network LOCAL_NET
esr(config-object-group-network)# ip prefix 21.12.2.0/24
esr(config-object-group-network)# exitesr(config)# object-group network PUBLIC_POOL
esr(config-object-group-network)# ip prefix 200.10.0.0/24
esr(config-object-group-network)# exitThe range of public network addresses for Static NAT use is specified in “PROXY” profile:
esr(config)# object-group network PROXY
esr(config-object-group-network)# ip address-range 200.10.0.100-200.10.0.150
esr(config-object-group-network)# exitConfigure Static NAT service in SNAT configuration mode. In the set attributes, specify that the rules are applying only to packets transferred to public network through te1/0/1 port. The rules include data source address test for belonging to “LOCAL_NET” pool and destination addresses test for belonging to “PUBLIC_POOL” pool.
esr(config)# nat source
esr(config-snat)# ruleset SNAT
esr(config-snat-ruleset)# to interface te1/0/1
esr(config-snat-ruleset)# rule 1
esr(config-snat-rule)# match source-address LOCAL_NET
esr(config-snat-rule)# match destination-address PUBLIC_POOL
esr(config-snat-rule)# action source-nat netmap 200.10.0.0/24 static
esr(config-snat-rule)# enable
esr(config-snat-rule)# exit
esr(config-snat-ruleset)# exitIn order the router could response to the ARP requests for addresses from the “PROXY” translation pool, you should launch ARP Proxy service. ARP Proxy service is configured on the interface that IP address from 'PROXY' address profile subnet belongs to:
esr(config)# interface tengigabitethernet 1/0/1
esr(config-if-te)# ip nat proxy-arp PROXYTo enable 200.10.0.0/24 network access for LAN devices, they should be configured for routing – 21.12.2.1 should be defined as a gateway address.
The configuration changes come into effect after applying the following commands:
esr# commit
Configuration has been successfully committed
esr# confirm
Configuration has been successfully confirmedYou can display active translations by using the following command:
esr# show ip nat translationsHTTP/HTTPS traffic proxying
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Create an object with a URL. | esr(config)# object-group url <NAME> | |
2 | Specify the set. | esr(config-object-group-url)# url <URL> | <URL> – web page, site address. |
3 | Create proxy profile. | esr(config)# ip http profile <NAME> | <NAME> – profile name. |
4 | Choose default action. | esr(config-profile)# default action {deny|permit|redirect} | <URL> – address of the host to which requests will be sent. |
5 | Specify description (optionally). | esr(config-profile)# description <description> | <description> – up to 255 characters. |
6 | Specify a remote or local URL list and type of operation (block/traffic pass/redirect) (optional). | esr(config-profile)# urls {local|remote} <URL_OBJ_GROUP_NAME> | <URL_OBJ_GROUP_NAME> – specify the name of the object containing the URL set. |
7 | Specify the remote server where the necessary URL lists are (optional). | esr(config)# ip http proxy server-url <URL> | <URL> – server address where remote url lists will be taken from. |
8 | Specify a listening port for proxying (optional). | esr(config)# ip http proxy listen-ports <OBJ_GROUP_NAME> | <OBJ_GROUP_NAME> – port profile name, set by string of up to 31 characters. |
9 | Specify a listening port for proxying (optional). | esr(config)# ip https proxy listen-ports <OBJ_GROUP_NAME> | <OBJ_GROUP_NAME> – port profile name, set by string of up to 31 characters. |
10 | Specify a base port for proxying (optional). | esr(config)# ip https proxy redirect-port <PORT> | <PORT> – port number, set in the range of [1..65535]. Default value: 3128 |
11 | Enable proxying on the interface based on the selected HTTP profile. | esr(config-if)# ip http proxy <PROFILE_NAME> | <PROFILE_NAME> – profile name |
12 | Enable proxying on the interface based on the selected HTTPS profile. | esr(config-if)# ip https proxy <PROFILE_NAME> | <PROFILE_NAME> – profile name |
13 | Create services lists which will be used during filtration. | esr(config)# object-group service <obj-group-name> | <obj-group-name> – service profile name, set by the string of up to 31 characters. |
14 | Specify services list description (optional). | esr(config-object-group-service)# description <description> | <description> – profile description, set by the string of up to 255 characters. |
15 | Add necessary services (tcp/udp ports) to the list. | esr(config-object-group-service)# port-range 3128-3135 | ESR proxy server uses for its operation the ports starting from the base port defined in step 10 The http proxy uses ports from base port to base port + the number of cpu of this ESR model - 1 For https proxy, the ports used are from base port + number of cpu of the given ESR model to base port + number of cpu of the given ESR model * 2 - 1 |
16 | Create an interzone interaction rule set. | esr(config)# security zone-pair <src-zone-name1> self | <src-zone-name> – security zone in which the interfaces with the ip http proxy or ip https proxy function are located. self – a predefined security zone for traffic entering the ESR itself. |
17 | Create an interzone interaction rule set. | esr(config-zone-pair)# rule <rule-number> | <rule-number> – 1..10000. |
18 | Specify rule description (optional). | esr(config-zone-rule)# description <description> | <description> – up to 255 characters.. |
19 | Specify the given rule force. | esr(config-zone-rule)# action <action> [ log ] | <action> – permit log – activation key for logging of sessions established according to this rule. |
20 | Set name of IP protocol for which the rule should work. | esr(config-zone-rule)# match protocol <protocol-type> | <protocol-type> – tcp ESR proxy server uses ESR protocol. |
21 | Set the destination TCP/UDP ports profile for which the rule should work (if the protocol is specified). | esr(config-zone-rule)# match [not] | <obj-group-name> – name of the service profile created in step 12. |
22 | Create an interzone interaction rule. | esr(config-zone-rule)# enable |
If the Firewall function on the ESR is not forcibly disabled, you must create an allow rule for the Self zone.
HTTP proxy configuration example
Objective:
Organize URL filtering for a number of addresses using a proxy.
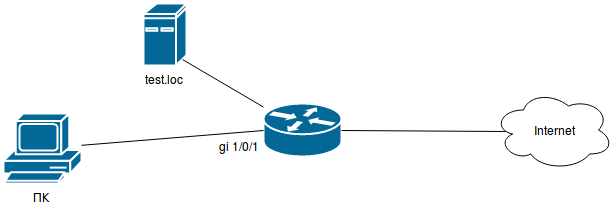
Solution:
Create a set of URLs to filter by. Configure a proxy filter and specify the actions for the created set of URLs:
esr# configure
esr(config)# object-group url test1
esr(config-object-group-url)# url http://speedtest.net/
esr(config-object-group-url)# url http://www.speedtest.net/
esr(config-object-group-url)# url https://speedtest.net/
esr(config-object-group-url)# url https://www.speedtest.net/
esr(config-object-group-url)# exitCreate a profile:
esr(config)# ip http profile list1
esr(config-profile)# default action permit
esr(config-profile)# urls local test1 action redirect redirect-url http://test.loc
esr(config-profile)# exitEnable proxying on the interface by profile 'list1':
esr(config)# interface gi 1/0/1
esr(config-if)# ip http proxy list1
esr(config-if)# ip https proxy list1If you use Firewall, create permissive rules for it:
For example we use the ESR-20 which has 4 CPUs.
For the http proxy we need to open ports 3128 to 3131
For the https proxy we need to open ports 3132 to 3135
Create a proxy server profile:
esr(config)# object-group service proxy
esr(config-object-group-service)# port-range 3128-3135
esr(config-object-group-service)# exitCreate a permissive interzonal interaction rule:
esr(config)# security zone-pair LAN self
esr(config-zone-pair)# rule 50
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# match protocol tcp
esr(config-zone-pair-rule)# match destination-port proxy
esr(config-zone-pair-rule)# enable
esr(config-zone-pair-rule)# exit
esr(config-zone-pair)# exitNTP (Network Time Protocol) — network protocol for synchronizing the internal clock of equipment using IP networks, uses the UDP protocol for its operation, takes into account transmission times and uses algorithms to achieve high precision time synchronization.
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Enable NTP. | esr(config)# ntp enable | |
2 | Set the IP address of the NTP server or NTP synchronization participant. | esr(config)# ntp { server | peer } { <IP> } | <IP> – destination IP address (gateway), defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
3 | Set authentication key (optional). | esr(config-ntp)# key <ID> | <ID> – key identifier, set in the range of [1..255]. |
4 | Set the maximum time interval between sending messages to the NTP server (optional). | esr(config-ntp)# maxpoll <INTERVAL> | <INTERVAL> – maximum value of poll interval. The command parameter is used as an indicator of the power of two when calculating the interval durability in seconds; it is calculated by raising two to power that is specified by the command parameter, takes the value of [10..17]. Default value: |
5 | Set the minimum time interval between sending messages to the NTP server (optional). | esr(config-ntp)# minpoll <INTERVAL> | <INTERVAL> – minimum value of poll interval in seconds; it is calculated by raising two to power that is specified by the command parameter, takes the value of [4..6]. Default value: 6 (26 = 64 seconds or 1 minutes 4 seconds) |
6 | Mark this NTP server as preferred (optional). | esr(config-ntp)# prefer | |
7 | Define a list of trusted IP addresses with which ntp packets can be exchanged (optional). | esr(config)# ntp access-addresses <NAME> | <NAME> – IP addresses profile name, set by the string of up to 31 characters. |
8 | Specify the key ID from the key binding profile (optional). | esr(config)# ntp authentication trusted-key <ID> | <ID> – key ID from the key binding profile. |
9 | Specify the key binding profile name (optional). | esr(config)# ntp authentication key-chain <WORD> | <WORD> – key binding profile name. |
10 | Activate key-based authentication for NTP (optional). | esr(config)# ntp authentication enable | |
11 | Enable the mode of receiving broadcast messages from NTP servers for the global configuration and all existing VRFs (optional). | esr(config)# ntp broadcast-client enable | |
12 | Set the DSCP code value for the use in IP headers of NTP server egress packets (optionally). | esr(config)# ntp dscp <DSCP> | <DSCP> – DSCP code value, takes values in the range of [0..63] Default value: 46 |
13 | Enable query-only mode that limits interaction via NTP for a certain profile of IP addresses (optional). | esr(config)# ntp object-group query-only <NAME> | <NAME> – IP addresses profile name, set by the string of up to 31 characters. |
14 | Enable serve-only mode that limits interaction via NTP for a certain profile of IP addresses (optional). | esr(config)# ntp object-group serve-only <NAME> | <NAME> – IP addresses profile name, set by the string of up to 31 characters. |
15 | Specify source-IP addresses for NTP packets for all peers (optional). | esr(config)# ntp source address <ADDR> | <ADDR> – IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
16 | Set the current time and date manually (optional). | esr# set date <TIME> [<DAY> <MONTH> [ <YEAR> ] ] | <TIME> – system timer, defined as HH:MM:SS, where:
<MONTH> – month, takes the following values [ January/February/March/April/May/June/July/August/September/October/November/December]; <YEAR> – year, takes values of [2001..2037]. |
Configuration example
Objective:
Set the time synchronization from the NTP server.
ESR router IP address – 192.168.52.8,
NTP server IP address – 192.168.52.41.
![]()
Solution:
First, do the following:
- specify security zone for gi1/0/1 interface;
- configure the IP address for the gi1/0/1 interface to provide IP connectivity to the NTP server.
Example:
security zone untrust
exit
object-group service NTP
port-range 123
exit
interface gigabitethernet 1/0/1
security-zone untrust
ip address 192.168.52.8/24
exit
security zone-pair untrust self
rule 10
action permit
match protocol udp
match destination-port NTP
enable
exit
exitMain configuration step:
Enable synchronization of the system clock with remote servers:
esr(config)# ntp enableNTP server configuration:
esr-(config)# ntp server 192.168.52.41Specify the preference for this NTP server (optional):
esr-1000(config-ntp)# preferSpecify the time interval between sending messages to the NTP server:
esr(config-ntp)# minpoll 4
esr(config-ntp)# end
esr# commit
esr# confirmCommand to view the current configuration of the NTP protocol:
esr# show ntp configurationCommand to view the current state of NTP servers (peers):
esr# show ntp peers