С ЧИПОМ. BRAS (Broadband Remote Access Server) management
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Add RADIUS server to the list of used servers and switch to its configuration mode. | esr(config)# radius-server host esr(config-radius-server)# | <IP-ADDR> – RADIUS server IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]; <IPV6-ADDR> – RADIUS server IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]. <VRF> – VRF instance name, set by the string of up to 31 characters. |
2 | Set the password for authentication on remote RADIUS server. | esr(config-radius-server)# key ascii-text | <TEXT> – string of [8..16] ASCII characters; <ENCRYPTED-TEXT> – encrypted password, [8..16] bytes size, set by the string of [16..32] characters. |
3 | Create AAA profile. | esr(config)# aaa radius-profile <NAME> | <NAME> – server profile name, set by the string of up to 31 characters. |
4 | Specify RADIUS server in AAA profile. | esr(config-aaa-radius-profile)# radius-server host | <IP-ADDR> – RADIUS server IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]; <IPV6-ADDR> – RADIUS server IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]. |
5 | Create DAS server. | esr(config)# das-server <NAME> | <NAME> – DAS server name, set by the string of up to 31 characters. |
6 | Set the password for authentication on remote DAS server. | esr(config-das-server)# key ascii-text | <TEXT> – string of [8..16] ASCII characters; <ENCRYPTED-TEXT> – encrypted password, [8..16] bytes size, set by the string of [16..32] characters. |
7 | Create AAA DAS profile. | esr(config)# aaa das-profile <NAME> | <NAME> – DAS profile name, set by the string of up to 31 characters. |
8 | Specify DAS server in DAs profile. | esr(config-aaa-das-profile)# das-server <NAME> | <NAME> – DAS server name, set by the string of up to 31 characters. |
9 | Configure BRAS. | esr(config)# subscriber-control [ vrf <VRF> ] | <VRF> – VRF instance name, set by the string of up to 31 characters, within which the user control will operate. |
10 | Select the profile of dynamic authorization servers to which CoS queries from PCRF will be sent. | esr(config-subscriber-control)# aaa das-profile <NAME> | <NAME> – DAS profile name, set by the string of up to 31 characters. |
11 | Select RADIUS server profile to obtain the user service parameters. | esr(config-subscriber-control)# aaa services-radius-profile | <NAME> – RADIUS server profile name, set by the string of up to 31 characters. |
12 | Select RADIUS server profile to obtain the user session parameters. | esr(config-subscriber-control)# aaa sessions-radius-profile | <NAME> – RADIUS server profile name, set by the string of up to 31 characters. |
13 | Set router IP address that will be used as source IP address in transmitted RADIUS packets. | esr(config-subscriber-control)# nas-ip-address <ADDR> | <ADDR> – source IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]; |
14 | Enable session authentication by MAC address (optionally). | esr(config-subscriber-control)# session mac-authentication | |
15 | Organize transparent filter-based transmission of administrative traffic (DHCP, DNS and etc.). | esr(config-subscriber-control)# bypass-traffic-a с l <NAME> | <NAME> – name of the ACL being bound, set by the string of up to 31 characters. |
16 | Switch to the default service configuration mode. | esr(config-subscriber-control)# default-service | |
17 | Bind the specified QoS class to the default service. | esr(config-subscriber-default-service)# class-map <NAME> | <NAME> – name of the class being bound, set by the string of up to 31 characters. |
18 | Specify a name of the URL list that will be used to filtrate HTTP/HTTPS traffic of non-authenticated users. | esr(config-subscriber-default-service)# filter-name | <LOCAL-NAME> – URL profile name, set by the string of up to 31 characters; <REMOTE-NAME> – remote server URL list name, set by the string of up to 31 characters. |
19 | Specify the actions that should be applied for HTTP/HTTPS packets, whose URL is included in the list of URL assigned by the “filter-name” command. | esr(config-subscriber-default-service)# filter-action<ACT> | <ACT> – allocated action:
redirect <URL> – redirect to the specified URL will be carried out, set by the string of up to 255 characters. |
20 | Specify the actions that should be applied for HTTP/HTTPS packets, whose URL is not included in the list of URL assigned by the “filter-name” command. | esr(config-subscriber-default-service)# default -action<ACT> | <ACT> – allocated action:
redirect <URL> – redirect to the specified URL will be carried out, set by the string of up to 255 characters. |
21 | Enable user control profile. | esr(config-subscriber-control)# enable | |
22 | Change the identifier of a network interface (physical, sub interface or network bridge) (optionally). | esr(config-if)# location <ID> | <ID> – network interface identifier, set by the string of up to 220 characters. |
23 | Enable user control on the interface. | esr(config-if-gi)# service-subscriber-control | <NAME> – IP addresses profile name, set by the string of up to 31 characters. |
24 | Enable iterative query of quota value when it expires for user services with a configured restriction on the amount of traffic or time (optionally). | esr(config-subscriber-control)# quota-expired-reauth | |
25 | Enable session authentication by IP address (optionally). | esr(config-subscriber-control)# session ip-authentication | |
26 | Enable transparent transmission of backup traffic for BRAS (optionally). | esr(config-subscriber-control)# backup traffic-processing | |
27 | Specify the interval after which currently unused URL lists will be removed (optionally). | esr(config)# subscriber-control unused-filters-remove-delay | <DELAY> – time interval in seconds, takes values of [10800..86400]. |
28 | Specify the interval after which, if a user has not sent any packets, the session is considered to be outdated and is removed from the device (optonally). | esr(config-subscriber-default-service)# session-timeout | <SEC> – time interval in seconds, takes values of [120..3600]. |
29 | Specify the VRRP group on the basis of which user control service status is determined (primary/redundant) (optionally). | esr(config-subscriber-control)# vrrp-group <GRID> | <GRID> – VRRP router group identifier, takes values in the range of [1..32]. |
30 | Define destination TCP ports from which the traffic will be redirected to the router HTTP Proxy server (optionally). | esr(config-subscriber-control)# ip proxy http listen-ports <NAME> | <NAME> – TCP/UDP ports profile name, set by the string of up to 31 characters. |
31 | Define HTTP Proxy server port on the router (optionally). | esr(config-subscriber-control)# ip proxy http redirect-port <PORT> | <PORT> – port number, set in the range of [1..65535]. |
32 | Define destination TCP ports from which the traffic will be redirected to the router HTTPS Proxy server (optionally). | esr(config-subscriber-control)# ip proxy https listen-ports <NAME> | <NAME> – TCP/UDP ports profile name, set by the string of up to 31 characters. |
33 | Define HTTPS Proxy server port on the router (optionally). | esr(config-subscriber-control)# ip proxy https redirect-port <PORT> | <PORT> – port number, set in the range of [1..65535]. |
34 | Set router IP address that will be used as source IP address in HTTP/HTTPS packets transmitted by Proxy server (optionally). | esr(config-subscriber-control)# ip proxy source-address <ADDR> | <ADDR> – source IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]; |
35 | Specify URL address of the server providing lists of traffic filtration applications (optionally). | esr(config)# subscriber-control apps-server-url <URL> | <URL> – reference address, set by the string from 8 to 255 characters. |
36 | Enable the application control on the interface (optionally). | esr(config-if-gi)# subscriber-control application-filter <NAME> | <NAME> – application profile name, set by the string of up to 31 characters. |
37 | Set/clear the upper bound of BRAS sessions amount (optionally). | esr(config-subscriber-control)# thresholds sessions-number high <Threshold> | <Threshold> – number of BRAS sessions:
|
38 | Set/clear the lower bound of BRAS sessions amount (optionally). | esr(config-subscriber-control)# thresholds sessions-number low <Threshold> | <Threshold> – number of BRAS sessions:
|
Example of configuration with SoftWLC
Objective:
Provide access to the Internet only to authorized users.
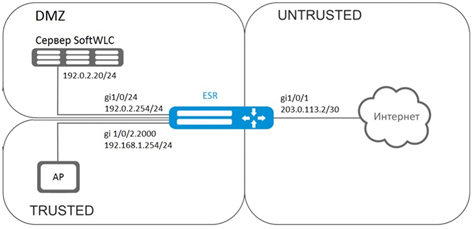
Solution:
SoftWLC server keeps accounts data and tariff plan parameters. You can obtain more detailed information on installation and configuring SoftWLC server using following links:
SoftWLC – general SoftWLC article;
SoftWLC installation and update – installation of SoftWLC from repositories.
The BRAS license is obligatory for router, after its activation you can start device configuring.
Create 3 security zones, according to the network structure:
esr# configure
esr(config)# security zone trusted
esr(config-zone)# exit
esr(config)# security zone untrusted
esr(config-zone)# exit
esr(config)# security zone dmz
esr(config-zone)# exitConfigure public port parameters and assign its default gateway:
esr(config)# interface gigabitethernet 1/0/1
esr(config-if-gi)# security-zone untrusted
esr(config-if-gi)# ip address 203.0.113.2/30
esr(config-if-gi)# service-policy dynamic upstream
esr(config-if-gi)# exit
esr(config)# ip route 0.0.0.0/0 203.0.113.1Configure port in direction to the SoftWLC server:
esr (config)# interface gigabitethernet 1/0/24
esr (config-if-gi)# security-zone dmz
esr (config-if-gi)# ip address 192.0.2.1/24
esr (config-if-gi)# exitConfigure port for Wi-Fi access point connection:
esr(config)# bridge 2
esr(config-bridge)# security-zone trusted
esr(config-bridge)# ip address 192.168.0.254/24
esr(config-bridge)# ip helper-address 192.0.2.20
esr(config-bridge)# service-subscriber-control object-group users
esr(config-bridge)# location ssid1
esr(config-bridge)# enable
esr(config-bridge)# exit
esr(config)# interface gigabitethernet 1/0/2.2000
esr(config-subif)# bridge-group 1
esr(config-subif)# exit
esr(config)# interface gigabitethernet 1/0/2
esr(config-if-gi)# service-policy dynamic downstream
esr (config-if-gi)# exitCustomer connection must be implemented through sub-interfaces to bridges. Selection of tariff plan depends on Location parameter (see bridge 2 configuration).
The module which is responsible for AAA operations is based on eltex-radius and available by SoftWLC IP address. Numbers of ports for authentication and accounting in the example below are the default values for SoftWLC.
Define parameters for interaction with the module:
esr(config)# radius-server host 192.0.2.20
esr(config-radius-server)# key ascii-text password
esr(config-radius-server)# auth-port 31812
esr (config-radius-server)# acct-port 31813
esr (config-radius-server)# exitCreate AAA profile:
esr(config)# aaa radius-profile RADIUS
esr(config-aaa-radius-profile)# radius-server host 192.0.2.20
esr(config-aaa-radius-profile)# exitSpecify access parameters to the DAS (Direct-attached storage) server:
esr(config)# object-group network server
esr(config-object-group-network)# ip address-range 192.0.2.20
esr(config-object-group-network)# exit
esr(config)# das-server CoA
esr(config-das-server)# key ascii-text password
esr(config-das-server)# port 3799
esr(config-das-server)# clients object-group server
esr(config-das-server)# exit
esr(config)# aaa das-profile CoA
esr(config-aaa-das-profile)# das-server CoA
esr(config-aaa-das-profile)# exitThe traffic from trusted zone is blocked before authentication as well as DHCP and DNS requests. You need to configure allowing rules in order to pass DHCP and DNS requests:
esr(config)# ip access-list extended DHCP
esr(config-acl)# rule 10
esr(config-acl-rule)# action permit
esr(config-acl-rule)# match protocol udp
esr(config-acl-rule)# match source-address any
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# match source-port 68
esr(config-acl-rule)# match destination-port 67
esr(config-acl-rule)# enable
esr(config-acl-rule)# exit
esr(config-acl)# rule 11
esr(config-acl-rule)# action permit
esr(config-acl-rule)# match protocol udp
esr(config-acl-rule)# match source-address any
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# match source-port any
esr(config-acl-rule)# match destination-port 53
esr(config-acl-rule)# enable
esr(config-acl-rule)#exit
esr(config-acl)# exitThen, create rules for redirecting to portal and passing traffic to the Internet:
esr(config)# ip access-list extended WELCOME
esr(config-acl)# rule 10
esr(config-acl-rule)# action permit
esr(config-acl-rule)# match protocol any
esr(config-acl-rule)# match source-address any
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# enable
esr(config-acl-rule)# exit
esr(config-acl)# exit
esr (config)# ip access-list extended INTERNET
esr(config-acl)# rule 10
esr(config-acl-rule)# action permit
esr(config-acl-rule)# match protocol any
esr(config-acl-rule)# match source-address any
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# enable
esr(config-acl-rule)# exit
esr(config-acl)# exitSpecify web resources which are available without authorization:
esr(config)# object-group url defaultservice
esr(config-object-group-url)# url http://eltex.nsk.ru
esr(config-object-group-url)# exitThe URL filtering lists are kept on SoftWLC server (you need to change only IP address of SoftWLC server, if addressing is different from the example. Leave the rest of URL without changes):
esr(config)# subscriber-control filters-server-url http://192.0.2.20:7070/Filters/file/Configure and enable BRAS, define NAS IP as address of the interface interacting with SoftWLC (gigabitethernet 1/0/24 in the example):
esr(config)# subscriber-control
esr(config-subscriber-control)# aaa das-profile CoA
esr(config-subscriber-control)# aaa sessions-radius-profile RADIUS
esr(config-subscriber-control)# nas-ip-address 192.0.2.1
esr(config-subscriber-control)# session mac-authentication
esr(config-subscriber-control)# bypass-traffic-acl DHCP
esr(config-subscriber-control)# default-service
esr(config-subscriber-default-service)# class-map INTERNET
esr(config-subscriber-default-service)# filter-name local defaultservice
esr(config-subscriber-default-service)# filter-action permit
esr(config-subscriber-default-service)# default-action redirect http://192.0.2.20:8080/eltex_portal/
esr(config-subscriber-default-service)# session-timeout 3600
esr(config-subscriber-default-service)# exit
esr(config-subscriber-control)# enable
esr(config-subscriber-control)# exitConfigure rules for transition between security zones:
esr(config)# object-group service telnet
esr(config-object-group-service)# port-range 23
esr(config-object-group-service)# exit
esr(config)# object-group service ssh
esr(config-object-group-service)# port-range 22
esr(config-object-group-service)# exit
esr(config)# object-group service dhcp_server
esr(config-object-group-service)# port-range 67
esr(config-object-group-service)# exit
esr(config)# object-group service dhcp_client
esr(config-object-group-service)# port-range 68
esr(config-object-group-service)# exit
esr(config)# object-group service ntp
esr(config-object-group-service)# port-range 123
esr(config-object-group-service)# exitEnable access to the Internet from trusted and dmz zones:
esr(config)# security zone-pair trusted untrusted
esr(config-zone-pair)# rule 10
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# match protocol any
esr(config-zone-pair-rule)# match source-address any
esr(config-zone-pair-rule)# match destination-address any
esr(config-zone-pair-rule)# enable
esr(config-zone-pair-rule)# exit
esr(config-zone-pair)# exit
esr(config)# security zone-pair dmz untrusted
esr(config-zone-pair)# rule 10
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# match protocol any
esr(config-zone-pair-rule)# match source-address any
esr(config-zone-pair-rule)# match destination-address any
esr(config-zone-pair-rule)# enable
esr(config-zone-pair-rule)# exit
esr(config-zone-pair)# exit
esr(config)# security zone-pair dmz trusted
esr(config-zone-pair)# rule 10
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# match protocol any
esr(config-zone-pair-rule)# match source-address any
esr(config-zone-pair-rule)# match destination-address any
esr(config-zone-pair-rule)# enable
esr(config-zone-pair-rule)# exit
esr(config-zone-pair)# exitEnable DHCP transmitting from trusted to dmz:
esr (config)# security zone-pair trusted dmz
esr (config-zone-pair)# rule 10
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# match protocol udp
esr(config-zone-pair-rule)# match source-address any
esr(config-zone-pair-rule)# match destination-address any
esr(config-zone-pair-rule)# match source-port dhcp_client
esr(config-zone-pair-rule)# match destination-port dhcp_server
esr(config-zone-pair-rule)# enable
esr(config-zone-pair-rule)# exit
esr(config-zone-pair)# exitEnable ICMP transmission to the device. For BRAS operation you need to open ports for web proxying - TCP 3129/3128 (NetPortDiscovery Port/Active API Server port:
esr(config)# object-group service bras
esr(config-object-group-service)# port-range 3129
esr(config-object-group-service)# port-range 3128
esr(config-object-group-service)# exit
esr(config)# security zone-pair trusted self
esr(config-zone-pair)# rule 10
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# match protocol tcp
esr(config-zone-pair-rule)# match source-address any
esr(config-zone-pair-rule)# match destination-address any
esr(config-zone-pair-rule)# match source-port any
esr(config-zone-pair-rule)# match destination-port bras
esr(config-zone-pair-rule)# enable
esr (config-zone-pair-rule)# exit
esr(config-zone-pair)# rule 20
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# match protocol icmp
esr(config-zone-pair-rule)# match source-address any
esr(config-zone-pair-rule)# match destination-address any
esr(config-zone-pair-rule)# enable
esr(config-zone-pair-rule)# exit
esr(config-zone-pair-rule)# exit
esr(config)# security zone-pair dmz self
esr(config-zone-pair)# rule 20
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# match protocol icmp
esr(config-zone-pair-rule)# match source-address any
esr(config-zone-pair-rule)# match destination-address any
esr(config-zone-pair-rule)# enable
esr(config-zone-pair-rule)# exit
esr(config-zone-pair-rule)# exit
esr(config)# security zone-pair untrusted self
esr(config-zone-pair)# rule 20
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# match protocol icmp
esr(config-zone-pair-rule)# match source-address any
esr(config-zone-pair-rule)# match destination-address any
esr(config-zone-pair-rule)# enable
esr(config-zone-pair-rule)# exit
esr(config-zone-pair-rule)# exitActivate DHCP-Relay:
esr(config)# ip dhcp-relay Configure SNAT for gigabitethernet 1/0/1 port:
esr(config)# nat source
esr(config-snat)# ruleset inet
esr(config-snat-ruleset)# to interface gigabitethernet 1/0/1
esr(config-snat-ruleset)# rule 10
esr(config-snat-rule)# match source-address any
esr(config-snat-rule)# action source-nat interface
esr(config-snat-rule)# enable
esr(config-snat-rule)# endExample of configuration without SoftWLC
Objective:
Configure BRAS without SoftWLC support.
Given:
Subnet with clients 10.10.0.0/16, subnet for working with FreeRADIUS server 192.168.1.1/24
Solution:
Step 1:
RADIUS server configuration.
For FreeRADIUS server, you need to specify the subnet that can send the queries and add a user list. To do this, add the following to the users file in the directory with FreeRADIUS server configuration files:
User profile:
<MACADDR> Cleartext-Password := <MACADDR> #User name
User-Name = <USER_NAME>, #Maximum session lifetime
Session-Timeout = <SECONDS>, #Maximum session lifetime when the system is idle
Idle-Timeout = <SECONDS>, #Session statistics update time
Acct-Interim-Interval = <SECONDS>, #Service name for a session (A – the service is enabled, N – the service is disabled)
Cisco-Account-Info = "{A|N}<SERVICE_NAME>" Service profile:
<SERVICE_NAME> Cleartext-Password := <MACADDR> # Matches class-map name in ESR settings
Cisco-AVPair = "subscriber:traffic-class=<CLASS_MAP>", # Action that is applied to the traffic by ESR (permit, deny, redirect)
Cisco-AVPair = "subscriber:filter-default-action=<ACTION>", # The ability of IP flows passing (enabled-uplink, enabled-downlink, enabled, disabled)
Cisco-AVPair = "subscriber:flow-status=<STATUS>" Add a subnet, in which ESR is located, to the clients.conf file:
client ESR {
ipaddr = <SUBNET>
secret = <RADIUS_KEY>
} In this case the RADIUS server configuration will be as follows:
Add the following strings to the “clients.conf” file:
client BRAS {
ipaddr = 192.168.1.1
secret = password
} Add the following strings to the “users” file (specify a client MAC address instead of <MAC>):
"54-E1-AD-8F-37-35" Cleartext-Password := "54-E1-AD-8F-37-35"
User-Name = "Bras_user",
Session-Timeout = 259200,
Idle-Timeout = 259200,
Cisco-AVPair += "subscriber:policer-rate-in=1000",
Cisco-AVPair += "subscriber:policer-rate-out=1000",
Cisco-AVPair += "subscriber:policer-burst-in=188",
Cisco-AVPair += "subscriber:policer-burst-out=188",
Cisco-Account-Info = "AINTERNET"
INTERNET Cleartext-Password := "INTERNET"
User-Name = "INTERNET",
Cisco-AVPair = "subscriber:traffic-class=INTERNET",
Cisco-AVPair += "subscriber:filter-default-action=permit"Step 2:
ESR configuration.
BRAS functional configuration requires the BRAS licence:
esr(config)# do sh licence
Licence information
-------------------
Name: Eltex
Version: 1.0
Type: ESR-X
S/N: NP00000000
MAC: XX:XX:XX:XX:XX:XX
Features:
BRAS – Broadband Remote Access ServerConfiguration of parameters for the interaction with RADIUS server:
esr(config)# radius-server host 192.168.1.2
esr(config-radius-server)# key ascii-text encrypted 8CB5107EA7005AFF
esr(config-radius-server)# source-address 192.168.1.1
esr(config-radius-server)# exitCreate AAA profile:
esr(config)# aaa radius-profile bras_radius
esr(config-aaa-radius-profile)# radius-server host 192.168.1.2
esr(config-aaa-radius-profile)# exit
esr(config)# aaa radius-profile bras_radius_servers
esr(config-aaa-radius-profile)# radius-server host 192.168.1.2
esr(config-aaa-radius-profile)# exitSpecify parameters for the DAS server:
esr(config)# das-server das
esr(config-das-server)# key ascii-text encrypted 8CB5107EA7005AFF
esr(config-das-server)# exit
esr(config)# aaa das-profile bras_das
esr(config-aaa-das-profile)# das-server das
esr(config-aaa-das-profile)# exit
esr(config)# vlan 10
esr(config-vlan)# exitThen, create rules for redirecting to portal and passing traffic to the Internet:
esr(config)# ip access-list extended BYPASS
esr(config-acl)# rule 1
esr(config-acl-rule)# action permit
esr(config-acl-rule)# match protocol udp
esr(config-acl-rule)# match source-address any
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# match source-port 68
esr(config-acl-rule)# match destination-port 67
esr(config-acl-rule)# enable
esr(config-acl-rule)# exit
esr(config-acl)# rule 2
esr(config-acl-rule)# action permit
esr(config-acl-rule)# match protocol udp
esr(config-acl-rule)# match source-address any
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# match source-port any
esr(config-acl-rule)# match destination-port 53
esr(config-acl-rule)# enable
esr(config-acl-rule)# exit
esr(config)# ip access-list extended INTERNET
esr(config-acl)# rule 1
esr(config-acl-rule)# action permit
esr(config-acl-rule)# match protocol any
esr(config-acl-rule)# match source-address any
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# enable
esr(config-acl-rule)# exit
esr(config)# ip access-list extended WELCOME
esr(config-acl)# rule 10
esr(config-acl-rule)# action permit
esr(config-acl-rule)# match protocol tcp
esr(config-acl-rule)# match source-address any
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# match source-port any
esr(config-acl-rule)# match destination-port 443
esr(config-acl-rule)# enable
esr(config-acl-rule)# exit
esr(config-acl)# rule 20
esr(config-acl-rule)# action permit
esr(config-acl-rule)# match protocol tcp
esr(config-acl-rule)# match source-address any
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# match source-port any
esr(config-acl-rule)# match destination-port 8443esr(config-acl-rule)# enable
esr(config-acl-rule)# exit
esr(config-acl)# rule 30
esr(config-acl-rule)# action permit
esr(config-acl-rule)# match protocol tcp
esr(config-acl-rule)# match source-address any
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# match source-port any
esr(config-acl-rule)# match destination-port 80
esr(config-acl-rule)# enable
esr(config-acl-rule)# exit
esr(config-acl)# rule 40
esr(config-acl-rule)# action permit
esr(config-acl-rule)# match protocol tcp
esr(config-acl-rule)# match source-address any
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# match source-port any
esr(config-acl-rule)# match destination-port 8080
esr(config-acl-rule)# enable
esr(config-acl-rule)# exitConfiguration of filtering by URL is obligatory. It is necessary to configure http-proxy filtering on BRAS for non-authorised users:
esr(config)# object-group url defaultserv
esr(config-object-group-url)# url http://eltex.nsk.ru
esr(config-object-group-url)# url http://ya.ru
esr(config-object-group-url)# url https://ya.ru
esr(config-object-group-url)# exitConfigure and enable BRAS, define NAS IP as address of the interface interacting with RADIUS server (gigabitethernet 1/0/2 in the example):
esr(config)# subscriber-control
esr(config-subscriber-control)# aaa das-profile bras_das
esr(config-subscriber-control)# aaa sessions-radius-profile bras_radius
esr(config-subscriber-control)# aaa services-radius-profile bras_radius_servers
esr(config-subscriber-control)# nas-ip-address 192.168.1.1
esr(config-subscriber-control)# session mac-authentication
esr(config-subscriber-control)# bypass-traffic-acl BYPASS
esr(config-subscriber-control)# default-service
esr(config-subscriber-default-service)# class-map BYPASS
esr(config-subscriber-default-service)# filter-name local defaultserv
esr(config-subscriber-default-service)# filter-action permit
esr(config-subscriber-default-service)# default-action redirect http://192.
168.1.2:8080/eltex_portal
esr(config-subscriber-default-service)# session-timeout 121
esr(config-subscriber-default-service)# exit
esr(config-subscriber-control)# enable
esr(config-subscriber-control)# exitPerform the following settings on the interfaces that require BRAS operation (minimum one interface is required for the successful start):
esr(config)# bridge 10
esr(config-bridge)# vlan 10
esr(config-bridge)# ip firewall disable
esr(config-bridge)# ip address 10.10.0.1/16
esr(config-bridge)# ip helper-address 192.168.1.2
esr(config-bridge)# service-subscriber-control any
esr(config-bridge)# location USER
esr(config-bridge)# protected-ports
esr(config-bridge)# protected-ports exclude vlan
esr(config-bridge)# enable
esr(config-bridge)# exitConfigure port towards the RADIUS server:
esr(config)# interface gigabitethernet 1/0/2
esr(config-if-gi)# ip firewall disable
esr(config-if-gi)# ip address 192.168.1.1/24
esr(config-if-gi)# exitPort towards the Client:
esr(config)# interface gigabitethernet 1/0/3.10
esr(config-subif)# bridge-group 10
esr(config-subif)# ip firewall disable
esr(config-subif)# exitConfigure SNAT for gigabitethernet 1/0/2 port:
esr(config)# nat source
esr(config-snat)# ruleset factory
esr(config-snat-ruleset)# to interface gigabitethernet 1/0/2
esr(config-snat-ruleset)# rule 10
esr(config-snat-rule)# description "replace 'source ip' by outgoing interface ip address"
esr(config-snat-rule)# match protocol any
esr(config-snat-rule)# match source-address any
esr(config-snat-rule)# match destination-address any
esr(config-snat-rule)# action source-nat interface
esr(config-snat-rule)# enable
esr(config-snat-rule)# exit
esr(config-snat-ruleset)# exit
esr(config-snat)# exit
esr(config)# ip route 0.0.0.0/0 192.168.1.2The configuration changes come into effect after applying the following commands:
esr(config) # do commit
esr(config) # do confirmTo view the information and statistics on the user control sessions, use the following command:
esr # sh subscriber-control sessions status
Session id User name IP address MAC address Interface Domain
-------------------- --------------- --------------- -----------------
1729382256910270473 Bras_user 10.10.0.3 54:e1:ad:8f:37:35 gi1/0/3.10 --