Redundancy management
VRRP configuration
VRRP (Virtual Router Redundancy Protocol) is a network protocol designed for increased availability of routers, acting as a default gateway. This is performed by aggregation of a router group into a single virtual router and assigning a shared IP address, that will be used as a default gateway for computers in the network.
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Switch to the interface/tunnel/network bridge configuration mode for which it is necessary to configure VRRP. | esr(config)# interface <IF-TYPE><IF-NUM> | <IF-TYPE> – interface type; <IF-NUM> – F/S/P – F frame (1), S – slot (0), P – port. |
esr(config)# tunnel <TUN-TYPE><TUN-NUM> | <TUN-TYPE> – tunnel type; <TUN-NUM> – tunnel number. | ||
esr(config)# bridge <BR-NUM> | <BR-NUM> – bridge number. | ||
2 | Configure the required parameters on the interface/network bridge, including IP address. | ||
3 | Enable VRRP process on IP interface. | esr(config-if-gi)# vrrp | |
esr(config-if-gi)# ipv6 vrrp | |||
4 | Set virtual IP address of VRRP router. | esr(config-if-gi)# vrrp ip <ADDR/LEN> | <ADDR/LEN> – virtual IP address, defined as AAA.BBB.CCC.DDD/EE where each part AAA-DDD takes values of [0..255] and EE takes values of [1..32]. You can specify several IP addresses separated by commas. Up to 4 IP addresses can be assigned to the interface. |
esr(config-if-gi)# ipv6 vrrp ip <IPV6-ADDR> | <IPV6-ADDR> – virtual IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]. Up to 8 IPv6 addresses separated by commas can be specified. | ||
5 | Set the VRRP router identifier. | esr(config-if-gi)# vrrp id <VRID> | <VRID> – VRRP router identifier, takes values in the range of [1..255]. |
esr(config-if-gi)# ipv6 vrrp id <VRID> | |||
6 | Set the VRRP router priority (optional). | esr(config-if-gi)# vrrp priority <PR> | <PR> – VRRP router priority, takes values in the range of [1..254]. Default value: 100. |
esr(config-if-gi)# ipv6 vrrp priority <PR> | |||
7 | Identify the VRRP router’s inherence to a group. The group provides the ability to synchronize several VRRP processes, so if in one of the processes there is a wizard change, then in another process roles will also be changed (optional). | esr(config-if-gi)# vrrp group <GRID> | <GRID> – VRRP router group identifier, takes values in the range of [1..32]. |
esr(config-if-gi)# ipv6 vrrp group <GRID> | |||
8 | Set the IP address that will be used as a source IP address for VRRP messages (optional). | esr(config-if-gi)# vrrp source-ip <IP> | <ADDR> – sender IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
esr(config-if-gi)# ipv6 vrrp source-ip <IPV6> | <IPV6> – source IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]. | ||
9 | Set the interval between sending VRRP messages (optional). | esr(config-if-gi)# vrrp timers advertise <TIME> | <TIME> – time in seconds, takes values of [1..40]. Default value: 1 second. |
esr(config-if-gi)# ipv6 vrrp timers advertise <TIME> | |||
10 | Set the interval after which GratuituousARP messages are sent when switching the router to the Master status (optional). | esr(config-if-gi)# vrrp timers garp delay <TIME> | <TIME> – time in seconds, takes values of [1..60]. Default value: 5 seconds. |
11 | Set the amount of GratuituousARP messages that will be sent when switching the router to the Master status (optional). | esr(config-if-gi)# vrrp timers garp repeat <COUNT> | <COUNT> – amount of messages, takes values of [1..60]. Default value: 5. |
12 | Set the interval after which GratuituousARP messages will be sent periodically while the router is in the Master status (optional). | esr(config-if-gi)# vrrp timers garp refresh <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: Periodic sending is disabled. |
13 | Set the amount of GratuituousARP messages that will be sent with the garprefresh period while the router is in the Master status (optional). | esr(config-if-gi)# vrrp timers garp refresh-repeat <COUNT> | <COUNT> – amount of messages, takes values of [1..60]. Default value: 1. |
14 | Specify whether the higher priority Backup router would try to take the Master role from the current lower priority Master router (optional). | esr(config-if-gi)# vrrp preemption disable | |
esr(config-if-gi)# ipv6 vrrp preemption disable | |||
15 | Set the time interval after which the higher priority Backup route will try to take the Master role from the current lower priority Master router (optional). | esr(config-if-gi)# vrrp preemption delay <TIME> | <TIME> – timeout, takes value in seconds [1..1000]. Default value: 0 |
esr(config-if-gi)# ipv6 vrrp preemption delay <TIME> | |||
16 | Set the password for neighbour authentication (optional). | esr(config-if-gi)# vrrp authentication key ascii-text | <CLEAR-TEXT> – password, set by the string of 8 to 16 characters; <ENCRYPTED-TEXT> – encrypted password of 8 to 16 bytes (from 16 to 32 characters) in hexadecimal format (0xYYYY ...) or (YYYY ...). |
17 | Specify authentication algorithm (optional). | esr(config-if-gi)# vrrp authentication algorithm <ALGORITHM> | <ALGORITHM> – authentication algorithm:
|
18 | Specify VRRP version (optional). | esr(config-if-gi)# vrrp version <VERSION> | <VERSION> – VRRP version: 2, 3. |
19 | Set the mode when vrrp IP address remains in the UP status regardless of the status of the interface itself (optional). | esr(config-if-gi)# vrrp force-up | |
20 | Specify the delay between the assignment of MASTER status to ipv6 vrrp and the start of ND messages distribution (optional). | esr(config-if-gi)# ipv6 vrrp timers nd delay <TIME> | <TIME> – time in seconds, takes values of [1..60]. Default value: 5. |
21 | Specify the period of ND protocol information update for ipv6 vrrp in MASTER status (optional). | esr(config-if-gi)# ipv6 vrrp timers nd refresh <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 5. |
22 | Specify the amount of ND messages sent in the update period for ipv6 vrrp in MASTER status (optional). | esr(config-if-gi)# ipv6 vrrp timers nd refresh-repeat <NUM> | <NUM> – amount, takes values of [1..60]. Default value: 0. |
23 | Specify the amount of ND packets sendings after setting ipv6 vrrp to the MASTER status (optional). | esr(config-if-gi)# ipv6 vrrp timers nd repeat <NUM> | <NUM> – amount, takes values of [1..60]. Default value: 1. |
Configuration example 1
Objective:
Establish LAN virtual gateway in VLAN 50 using VRRP. IP address 192.168.1.1 is used as a local virtual gateway.
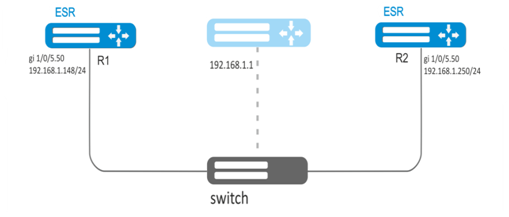
Solution:
First, do the following:
- create a correspond sub interface;
- configure a zone for the sub-interface;
- specify IP address for the sub-interface.
Main configuration step:
Configure R1 router.
Configure VRRP in the created sub-interface. Specify unique VRRP identifier:
R1(config)#interface gi 1/0/5.50
R1(config-subif)# vrrp id 10Specify virtual gateway IP address 192.168.1.1/24:
R1(config-subif)# vrrp ip 192.168.1.1Enable VRRP:
R1(config-subif)# vrrp
R1(config-subif)# exitAfter that it is necessary to make the same settings on R2.
Configuration example 2
Objective:
Establish virtual gateways for 192.168.20.0/24 subnet in VLAN 50 and 192.168.1.0/24 in VLAN 60 using VRRP with Master sync feature. To do this, group VRRP processes. IP addresses 192.168.1.1 and 192.168.20.1 are used as virtual gateways.
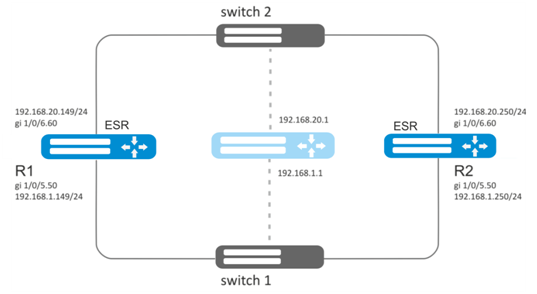
Solution:
First, do the following:
- create correspond sub interfaces;
- configure a zone for the sub-interfaces;
- specify IP addresses for the sub-interfaces.
Main configuration step:
Configure R1 router.
Configure VRRP for 192.168.1.0/24 subnet in the created sub-interface.
Specify unique VRRP identifier:
R1(config-sub)#interface gi 1/0/5.50
R1(config-subif)# vrrp id 10Specify virtual gateway IP address 192.168.1.1:
R1(config-subif)# vrrp ip 192.168.1.1Specify VRRP group identifier:
R1(config-subif)# vrrp group 5Enable VRRP:
R1(config-subif)# vrrp
R1(config-subif)# exitConfigure VRRP for 192.168.20.0/24 subnet in the created sub-interface.
Specify unique VRRP identifier:
R1(config-sub)#interface gi 1/0/6.60
R1(config-subif)# vrrp id 20Specify virtual gateway IP address 192.168.1.20:
R1(config-subif)# vrrp ip 192.168.20.1Specify VRRP group identifier:
R1(config-subif)# vrrp group 5Enable VRRP:
R1(config-subif)# vrrp
R1(config-subif)# exitConfigure R2 in the same manner.
In addition to tunnel creation, enable VRRP protocol (112) in the firewall.
When using IPsec with VRRP, it is recommended to configure DPD to speed up IPsec tunnel rebuilding.
Tracking configuration
Tracking is a mechanism, which allows activating entities, depending on VRRP/SLA state.
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Configure VRRP according to the section VRRP configuration algorithm or configure SLA. |
| |
2 | Add Tracking object to the system and switch to the Tracking object parameters configuration mode. | esr(config)#tracking <ID> | <ID> – Tracking object number, takes values of [1..100]. |
3 | Set a rule for tracking VRRP/SLA processes, based on which Tracking object will switch to active state. | esr(config-track)# track vrrp id <VRID> state [not] { master | backup | fault } [vrf <VRF> ] | <VRID> – trackable VRRP router identifier, takes values in the range of [1..255]; <VRF> – VRF name, set by the string of up to 31 characters. |
| esr(config-track)# track sla test <NUM> [ mode <MODE> ] | <NUM> – SLA test name, set in range of [1..10000]; <MODE> – SLA test tracking mode, may take the following values:
| ||
4 | Enable Tracking object. | esr(config-tracking)#enable | |
| 5 | Set delay for changing state of the monitored object (optional). | esr(config-track)# delay { down | up } <TIME> | <TIME> – delay in seconds, set in range of [1..300]. |
| 6 | Set tracking operation mode (optional). | esr(config-track)# mode <MODE> | <MODE> – condition for the Tracking object to be in the active state, takes the following values:
|
| 7 | Create an entity on the ESR that will change depending on the state of the Tracking object. | ||
7.1 | Add the ability to manage a static IP route to the specified subnet (optional). | esr(config)# ip route [ vrf <VRF> ] <SUBNET> { <NEXTHOP> [ resolve ] | | <VRF> – VRF name, set by the string of up to 31 characters. <SUBNET> – destination address, can be specified in the following formats: AAA.BBB.CCC.DDD – host IP address, where each part takes values of [0..255]. AAA.BBB.CCC.DDD/NN – network IP address with prefix mask, where AAA-DDD take values of [0..255] and NN takes values of [1..32]. <NEXTHOP> – gateway IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255];
<IF> – an IP interface name specified in the form described in Section Types and naming order of router interfaces; <TUN> – the name of the tunnel is specified as described in section Types and naming order of router tunnels; <RULE> – wan rule number, set in the range of [1..50];
<METRIC> – route metric, takes values of [0..255]; <TRACK-ID> – Tracking object identifier. If the router is bound to the Tracking object, it will appear in the system only after meeting all requirements specified in the object. |
| 7.2 | Add the ability to manage the logical state of the interface (optional). | esr(config-if-gi)# shutdown track <ID> | <ID> – Tracking object number, takes values of [1..100]. |
| 7.3 | Add the ability to control the priority of the VRRP process (optional). | esr(config-if-gi)# vrrp priority track <ID> { <PRIO> | increment <INC> | decrement <DEC> } | <ID> – Tracking object number, takes values of [1..100]; <PRIO> – priority of the VRRP process, which will be set if the Tracking object is in the active state, takes values of [1..254]; <INC> – value by which the priority of the VRRP process will increase if the Tracking object is in the active state, takes values of [1..254]; <DEC> – value by which the priority of the VRRP process will decrease if the Tracking object is in the active state, takes values of [1..254]. |
| 7.4 | Add the ability to control Next-Hop for packets that match criteria in the specified access list (ACL) (optional). | esr(config-route-map-rule)# action set ip next-hop verify-availability <NEXTHOP><METRIC> track <ID> | <NEXTHOP> – gateway IP address in the AAA.BBB.CCC.DDD format, where each part takes values of [0..255]; <METRIC> – route metric, takes values of [0..255]; <ID> – Tracking object number, takes values of [1..100]. |
7.5 | Add the ability to control the BGP AS-Path attribute that will be added to the front of the AS-Path list (optional). | esr(config-route-map-rule)# action set as-path | <AS-PATH> – list of autonomous system numbers to be added to the current value in the route. Specified as AS,AS,AS, takes values of [1..4294967295]; <ID> – Tracking object number, takes values of [1..100]. |
| 7.6 | Add the ability to control the BGP MED attribute in the route for which the rule should fire (optional). | esr(config-route-map-rule)# action set metric bgp <METRIC> track <ID> | <METRIC> – BGPMED attribute value, takes values of [0..4294967295]; <ID> – Tracking object number, takes values of [1..100]. |
Configuration example
Objective:
Virtual gateway 192.168.0.1/24 is organized for 192.168.0.0/24 subnet, using VRRP protocol and routers R1 and R2. There is a link with a singular subnet 192.168.1.0/30 between R1 and R2 routers. Subnet 10.0.1.0/24 is terminated only on R2 router. PC has IP address - 192.168.0.4/24 and default gateway 192.168.1.1.
When router R1 is in vrrp backup state, traffic from PC will be transmitted without any additional settings. When router R1 is in vrrp master state, additional route is necessary for subnet 10.0.1.0/24 through interface 192.168.1.2.
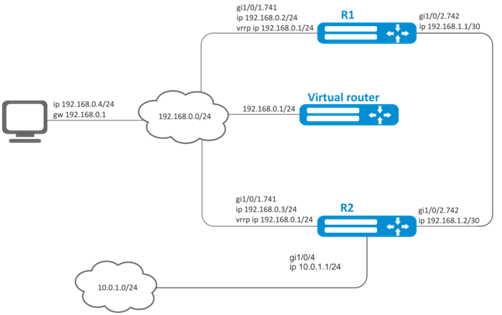
Initial configurations of the routers:
R1 router
hostname R1
interface gigabitethernet 1/0/1
switchport forbidden default-vlan
exit
interface gigabitethernet 1/0/1.741
ip firewall disable
ip address 192.168.0.2/24
vrrp id 10
vrrp ip 192.168.0.1/24
vrrp
exit
interface gigabitethernet 1/0/2
switchport forbidden default-vlan
exit
interface gigabitethernet 1/0/2.742
ip firewall disable
ip address 192.168.1.1/30
exitR2 router
hostname R2
interface gigabitethernet 1/0/1
switchport forbidden default-vlan
exit
interface gigabitethernet 1/0/1.741
ip firewall disable
ip address 192.168.0.3/24
vrrp id 10
vrrp ip 192.168.0.1/24
vrrp
exit
interface gigabitethernet 1/0/2
switchport forbidden default-vlan
exit
interface gigabitethernet 1/0/2.742
ip firewall disable
ip address 192.168.1.2/30
exit
interface gigabitethernet 1/0/4
ip firewall disable
ip address 10.0.1.1/24
exit
Solution:
There is no need in any changes in router R2, since subnet 10.0.1.0/24 is terminated on it and as soon as router R2 is vrrp master, packets will be transmitted to corresponding interface. As soon as R1 becomes vrrp master, route for packets must be created with destination IP address from network 10.0.1.0/24.
Create track-object with corresponding condition:
R1(config)# track 1
R1(config-track)# track vrrp id 10 state master
R1(config-track)# enable
R1(config-track)# exitCreate static route to subnet 10.0.1.0/24 through 192.168.1.2, which will work in case of satisfying of track 1 condition:
R1(config)# ip route 10.0.1.0/24 192.168.1.2 track 1 Firewall/NAT failover configuration
Firewall failover is required to reserve firewall sessions.
Configuration algorithm
Step | Description | Command | Key |
|---|---|---|---|
1 | Select the routers communication mode. | ip firewall failover sync-type <MODE> | <MODE> – communication mode:
|
| 2 | Select the IP address of the network interface from which messages will be sent when the Firewall is running in session reservation mode. | ip firewall failover source-address <ADDR> | <ADDR> – IP address of the sender network interface, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
| 3 | Set neighbor's IP address when reserving Firewall sessions in unicast mode. | ip firewall failover destination-address <ADDR> | <ADDR> – neighbor IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
| Configuring multicast IP address that will be used to exchange information when the Firewall session backup is in multicast mode. | ip firewall failover multicast-address <ADDR> | <ADDR> – multicast IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. | |
| 4 | If Firewall session reservation works in multicast mode, then it is necessary to configure the multicast group ID. | ip firewall failover multicast-group <GROUP> | <GROUP> – multicast group, specified in range [1000..9999]. |
| 5 | Setting the UDP port number of the Firewall session reservation service through which information is exchanged when working in unicast mode (optional). | ip firewall failover port <PORT> | <PORT> – port number of Firewall session reservation service, specified in range [1..65535]. |
| 6 | Binding of a VRRP group, based on which the state (main/backup) of the router is determined when reserving Firewall sessions (optional). | ip firewall failover vrrp-group <GRID> | <GRID> – VRRP router group ID, takes values of [1..32]. |
| 7 | Enabling Firewall session reservation. | ip firewall failover |
When configuring firewall failover, NAT sessions between devices will also be synchronized.
Configuration example
Objective:
Configure firewall session reservation for VRRP group in unicast mode. It is necessary to organize redundancy for two subnets using the VRRP protocol, synchronize VRRP processes on routers.
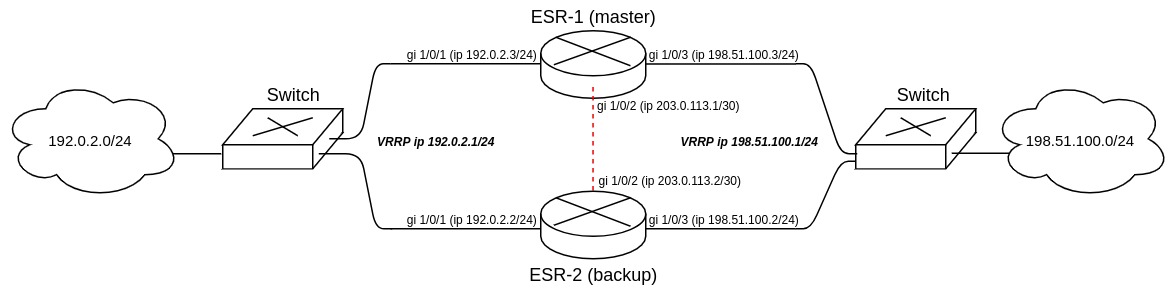
Main configuration steps:
- Configure VRRP processes on routers. Use vrrp priority 20 for master, and vrrp priority 10 for backup.
- Configure firewall failover in unicast mode with udp port number 3333 for VRRP group.
- Configure security zone for VRRP and UDP protocols.
Solution:
Configure ESR-1 router (master).
First, configure IP address on interfaces and define belonging to the security zone.
master(config)# interface gigabitethernet 1/0/1
master(config-if-gi)# security-zone trusted
master(config-if-gi)# ip address 192.0.2.3/24
master(config-if-gi)# exit
master(config)# interface gigabitethernet 1/0/2
master(config-if-gi)# security-zone trusted
master(config-if-gi)# ip address 203.0.113.1/30
master(config-if-gi)# exit
master(config)# interface gigabitethernet 1/0/3
master(config-if-gi)# security-zone trusted
master(config-if-gi)# ip address 198.51.100.3/24
master(config-if-gi)# exitConfigure VRRP processes on interfaces. The following parameters on the router interfaces should be configured: VRRP ID, VRRP IP address, VRRP priority, VRRP router belonging to a group.
Additionally, vrrp preempt delay should be configured on the master, as a result of which there will be time to establish firewall synchronization before the backup router transfers master role.
After that, enable the vrrp process using the 'vrrp' command.
It is possible to select vrrp preempt disable operation mode instead of configuring vrrp preempt delay. As a result, router with higher VRRP priority will not take away the master role from the router with lower VRRP priority after returning to operation.
To ensure that the VRRP processes states on a router are synchronized (master, backup), as well as to synchronize their sessions using firewall failover, it is necessary to configure them to belong to the same VRRP group.
master(config)# interface gigabitethernet 1/0/1
master(config-if-gi)# vrrp id 1
master(config-if-gi)# vrrp ip 192.0.2.1/24
master(config-if-gi)# vrrp priority 20
master(config-if-gi)# vrrp group 1
master(config-if-gi)# vrrp preempt delay 60
master(config-if-gi)# vrrp
master(config-if-gi)# exit
master(config)# interface gigabitethernet 1/0/3
master(config-if-gi)# vrrp id 3
master(config-if-gi)# vrrp ip 198.51.100.1/24
master(config-if-gi)# vrrp priority 20
master(config-if-gi)# vrrp group 1
master(config-if-gi)# vrrp preempt delay 60
master(config-if-gi)# vrrp
master(config-if-gi)# exitConfigure firewall failover.
Select the unicast session reservation mode:
master(config)# ip firewall failover sync-type unicastSelect the IP addresses of the network interface from which messages will be sent when the Firewall is running in session reservation mode:
master(config)# ip firewall failover source-address 203.0.113.1Configure the neighbor's IP addresses when reserving Firewall sessions in unicast mode:
master(config)# ip firewall failover destination-address 203.0.113.2Configure the UDP port number of the Firewall session reservation service:
master(config)# ip firewall failover port 3333Enable Firewall session reservations:
master(config)# ip firewall failoverTo configure security zone rules, create a profile for the firewall failover port:
master(config)# object-group service failover
master(config-object-group-service)# port-range 3333
master(config-object-group-service)# exitAdditionally, the following protocols must be allowed in the security zone-pair trusted self:
master(config)# security zone-pair trusted self
master(config-zone-pair)# rule 66
master(config-zone-pair-rule)# action permit
master(config-zone-pair-rule)# match protocol vrrp
master(config-zone-pair-rule)# enable
master(config-zone-pair-rule)# exit
master(config-zone-pair)# rule 67
master(config-zone-pair-rule)# action permit
master(config-zone-pair-rule)# match protocol udp
master(config-zone-pair-rule)# match destination-port failover
master(config-zone-pair-rule)# enable
master(config-zone-pair-rule)# exit
master(config-zone-pair)# exitView the status of VRRP processes using the following command:
master# show vrrp
Virtual router Virtual IP Priority Preemption State
-------------- --------------------------------- -------- ---------- ------
1 192.0.2.1/24 20 Enabled Master
3 198.51.100.1/24 20 Enabled Master View the status of Firewall session reservations using the following command
master# show ip firewall failover
Communication interface: gigabitethernet 1/0/2
Status: Running
Bytes sent: 2496
Bytes received: 640
Packets sent: 271
Packets received: 40
Send errors: 0
Receive errors: 0View the status of device redundancy systems using the following command:
master# show high-availability state
AP Tunnels:
State: Disabled
Last state change: --
DHCP server:
State: Disabled
Last state change: --
Firewall sessions:
State: successful synchronization
Last synchronization: 09:38:00 05.08.2021Configure ESR-2 router (backup).
Configure interfaces:
backup(config)# interface gigabitethernet 1/0/1
backup(config-if-gi)# security-zone trusted
backup(config-if-gi)# ip address 192.0.2.2/24
backup(config-if-gi)# vrrp id 1
backup(config-if-gi)# vrrp ip 192.0.2.1/24
backup(config-if-gi)# vrrp priority 10
backup(config-if-gi)# vrrp group 1
backup(config-if-gi)# vrrp
backup(config-if-gi)# exitbackup(config)# interface gigabitethernet 1/0/2
backup(config-if-gi)# security-zone trusted
backup(config-if-gi)# ip address 203.0.113.2/30
backup(config-if-gi)# exibackup(config)# interface gigabitethernet 1/0/3
backup(config-if-gi)# security-zone trusted
backup(config-if-gi)# ip address 198.51.100.2/24
backup(config-if-gi)# vrrp id 3
backup(config-if-gi)# vrrp ip 198.51.100.1/24
backup(config-if-gi)# vrrp priority 10
backup(config-if-gi)# vrrp group 1
backup(config-if-gi)# vrrp
backup(config-if-gi)# exitConfigure firewall failover:
backup(config)# ip firewall failover sync-type unicast
backup(config)# ip firewall failover source-address 203.0.113.2
backup(config)# ip firewall failover destination-address 203.0.113.1
backup(config)# ip firewall failover port 3333
backup(config)# ip firewall failover vrrp-group 1
backup(config)# ip firewall failoverConfiguration of a security zone is similar to the configuration of security zone for the ESR-1 (master) router.
DHCP failover configuration
DHCP failover is used to reserve a database of IP addresses that were dynamically issued during the operation of the DHCP server.
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | To configure DHCP failover, switch to its configuration menu. | ip dhcp-server failover [ vrf <VRF> ] | <VRF> – VRF name, set by the string of up to 31 characters. |
| 2 | Select DHCP failover operation mode. | mode { active-active | active-standby } | active-active – operating mode with two active routers; active-standby – operating mode with one active router and one standby router. |
| 3 | Configure the IP address from which DHCP failover will work. | local-address <ADDR> | <ADDR> – neighbor IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
| 4 | Configure the remote IP address of the neighbor that DHCP failover will work with. | remote-address <ADDR> | <ADDR> – neighbor IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
| 5 | Configure the DHCP failover role when redundancy works in Active-Active mode. | role <ROLE> | <ROLE> – DHCP server role when operating in standby mode:
|
| 6 | Bind the VRRP group, on the basis of which the state (primary/backup) of the router is determined when reserving sessions in the Active-Standby mode. | vrrp-group <GRID> | <GRID> – VRRP router group identifier, takes values in the range of [1..32]. |
| 7 | Enable DHCP failover redundancy. | enable |
The active-standby mode in VRF is not supported.
Configuration example
Objective:
Configure DHCP server reservation in Active-Standby mode. It is necessary to organize redundancy for two subnets using the VRRP protocol, synchronize VRRP processes on routers.

Main configuration steps:
- Configure VRRP processes on routers. Use vrrp priority 20 for master, and vrrp priority 10 for backup.
- Configure DHCP failover in Active-Standby mode.
- Configure security zone for VRRP, UDP and TCP protocols.
Solution:
Configure ESR-1 router (master).
First, configure IP address on interfaces and define belonging to the security zone.
master(config)# interface gigabitethernet 1/0/1
master(config-if-gi)# security-zone trusted
master(config-if-gi)# ip address 192.0.2.3/24
master(config-if-gi)# exit
master(config)# interface gigabitethernet 1/0/2
master(config-if-gi)# security-zone trusted
master(config-if-gi)# ip address 203.0.113.1/30
master(config-if-gi)# exit
master(config)# interface gigabitethernet 1/0/3
master(config-if-gi)# security-zone trusted
master(config-if-gi)# ip address 198.51.100.3/24
master(config-if-gi)# exitConfigure VRRP processes on interfaces. The following parameters on the router interfaces should be configured: VRRP ID, VRRP IP address, VRRP priority, VRRP router belonging to a group.
After that, enable the vrrp process using the 'vrrp' command.
It is possible to select vrrp preempt disable operation mode instead of configuring vrrp preempt delay. As a result, router with higher VRRP priority will not take away the master role from the router with lower VRRP priority after returning to operation.
To ensure that the VRRP processes states on a router are synchronized (master, backup), it is necessary to configure them to belong to the same VRRP group.
master(config)# interface gigabitethernet 1/0/1
master(config-if-gi)# vrrp id 1
master(config-if-gi)# vrrp ip 192.0.2.1/24
master(config-if-gi)# vrrp priority 20
master(config-if-gi)# vrrp group 1
master(config-if-gi)# vrrp
master(config-if-gi)# exit
master(config)# interface gigabitethernet 1/0/3
master(config-if-gi)# vrrp id 3
master(config-if-gi)# vrrp ip 198.51.100.1/24
master(config-if-gi)# vrrp priority 20
master(config-if-gi)# vrrp group 1
master(config-if-gi)# vrrp
master(config-if-gi)# exitConfigure DHCP failover. For DHCP failover it is necessary to configure the following parameters: mode, local-address, remote-address, VRRP router belonging to a group.
master(config)# ip dhcp-server pool LAN
master(config-dhcp-server)# network 192.0.2.0/24
master(config-dhcp-server)# address-range 192.0.2.10-192.0.2.20
master(config-dhcp-server)# exit
master(config)# ip dhcp-server
master(config)# ip dhcp-server failover
master(config-dhcp-server-failover)# mode active-standby
master(config-dhcp-server-failover)# local-address 203.0.113.1
master(config-dhcp-server-failover)# remote-address 203.0.113.2
master(config-dhcp-server-failover)# vrrp-group 1
master(config-dhcp-server-failover)# enable
master(config-dhcp-server-failover)# exitTo start DHCP failover, first configure and enable the DHCP server that will be backed up.
To configure security zone rules, create a profile for the DHCP failover port:
master(config)# object-group service dhcp_failover
master(config-object-group-service)# port-range 873
master(config-object-group-service)# exitDHCP failover uses TCP port 873 for synchronization, it must be enabled when configuring firewall.
Additionally, the following protocols must be allowed in the security zone-pair trusted self:
master(config)# security zone-pair trusted self
master(config-zone-pair)# rule 66
master(config-zone-pair-rule)# action permit
master(config-zone-pair-rule)# match protocol vrrp
master(config-zone-pair-rule)# enable
master(config-zone-pair-rule)# exit
master(config-zone-pair)# rule 67
master(config-zone-pair-rule)# action permit
master(config-zone-pair-rule)# match protocol tcp
master(config-zone-pair-rule)# match destination-port dhcp_failover
master(config-zone-pair-rule)# enable
master(config-zone-pair-rule)# exit
master(config-zone-pair)# rule 68
master(config-zone-pair-rule)# action permit
master(config-zone-pair-rule)# match protocol udp
master(config-zone-pair-rule)# enable
master(config-zone-pair-rule)# exit View the status of VRRP processes using the following command:
master# show vrrp
Virtual router Virtual IP Priority Preemption State
-------------- --------------------------------- -------- ---------- ------
1 192.0.2.1/24 20 Enabled Master
3 198.51.100.1/24 20 Enabled Master View the status of Firewall session reservations using the following command:
master# show ip dhcp server failover
VRF: --
State: SuccessfulView the status of device redundancy systems using the following command:
master# show high-availability state
AP Tunnels:
State: Disabled
Last state change: --
DHCP option 82 table:
State: Disabled
Last state change: --
DHCP server:
VRF: --
State: Successful synchronization
State: Disabled
Last synchronization: --For successful synchronization of the DHCP failover service, identical time must be set on the devices.
ESR-2 router (backup) configuration.
Configure interfaces:
backup(config)# interface gigabitethernet 1/0/1
backup(config-if-gi)# security-zone trusted
backup(config-if-gi)# ip address 192.0.2.2/24
backup(config-if-gi)# vrrp id 1
backup(config-if-gi)# vrrp ip 192.0.2.1/24
backup(config-if-gi)# vrrp priority 20
backup(config-if-gi)# vrrp group 1
backup(config-if-gi)# vrrp
backup(config-if-gi)# exit
backup(config)# interface gigabitethernet 1/0/2
backup(config-if-gi)# security-zone trusted
backup(config-if-gi)# ip address 203.0.113.2/30
backup(config-if-gi)# exit
backup(config)# interface gigabitethernet 1/0/3
backup(config-if-gi)# security-zone trusted
backup(config-if-gi)# ip address 198.51.100.2/24
backup(config-if-gi)# vrrp id 3
backup(config-if-gi)# vrrp ip 198.51.100.1/24
backup(config-if-gi)# vrrp priority 10
backup(config-if-gi)# vrrp group 1
backup(config-if-gi)# vrrp
backup(config-if-gi)# exitConfigure DHCP failover:
backup(config)# ip dhcp-server pool LAN
backup(config-dhcp-server)# network 192.0.2.0/24
backup(config-dhcp-server)# address-range 192.0.2.10-192.0.2.20
backup(config-dhcp-server)# exit
backup(config)# ip dhcp-server
backup(config)# ip dhcp-server failover
backup(config-dhcp-server-failover)# mode active-standby
backup(config-dhcp-server-failover)# local-address 203.0.113.2
backup(config-dhcp-server-failover)# remote-address 203.0.113.1
backup(config-dhcp-server-failover)# vrrp-group 1
backup(config-dhcp-server-failover)# enable
backup(config-dhcp-server-failover)# exitConfiguration of a security zone is similar to the configuration of security zone for the ESR-1 (master) router.