Routing management. Firmware version 1.13.0
Routing information advertising policy
RIP
in/out | Default policy | Advertising methods | Filtering methods | Filtering policy application levels |
|---|---|---|---|---|
Import | Route information reception is not limited | Network, Redistribute | Route-map — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. Prefix-list — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. | RIP process |
Export | Without separate advertising commands, the router does not send routing information | Prefix-list — the last (implicit) rule allows anything that is not explicitly denied by the previous rules. Prefix-list — the last (implicit) rule allows anything that is not explicitly denied by the previous rules. |
OSPF protocol
in/out | Default policy | Advertising methods | Filtering methods | Filtering policy application levels |
|---|---|---|---|---|
Import | Route information reception is not limited | Network, Redistribute | Route-map — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. Prefix-list — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. | OSPF process |
Export | Information about interfaces with OSPF protocol enabled is advertised | Route-map — the last (implicit) rule allows anything that is not explicitly denied by the previous rules. Prefix-list — the last (implicit) rule allows anything that is not explicitly denied by the previous rules. Filtering of advertised route information is possible for the following types of OSPF routes: E2, E1 |
IS-IS protocol
in/out | Default policy | Advertising methods | Filtering methods | Filtering policy application levels |
|---|---|---|---|---|
Import | Route information reception is not limited | Network, Redistribute | Route-map — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. Prefix-list — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. | IS-IS process |
Export | Information about interfaces with IS-IS protocol enabled is advertised | Route-map — the last (implicit) rule allows anything that is not explicitly denied by the previous rules. Prefix-list — the last (implicit) rule allows anything that is not explicitly denied by the previous rules. |
iBPG protocol
in/out | Default policy | Advertising methods | Filtering methods | Filtering policy application levels |
|---|---|---|---|---|
Import | Route information reception is not limited | Network, Redistribute | Route-map — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. Prefix-list — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. | address-family, peer-group, neighbor |
Export | All the routes that have entered the RIB via the BGP protocol are advertised | Route-map — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. Prefix-list — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. |
eBPG protocol
in/out | Default policy | Advertising methods | Filtering methods | Filtering policy application levels |
|---|---|---|---|---|
Import | Route information reception is not limited | Network, Redistribute | Route-map — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. Prefix-list — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. | address-family, peer-group, neighbor |
Export | Routes are denied until an allowing route-map or prefix-list is applied | Route-map — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. Prefix-list — the last (implicit) rule denies anything that is not explicitly allowed by the previous rules. |
Static routes configuration
Static routing is a type of routing in which routes are defined explicitly during the router configuration without dynamic routing protocols.
Configuration algorithm
You can add a static route by using the following command in global configuration mode:
esr(config)# ip route [ vrf <VRF> ] <SUBNET> { <NEXTHOP> | interface <IF> | tunnel <TUN> | wan load-balance rule <RULE> [<METRIC>] | blackhole | unreachable | prohibit } [ <METRIC> ] [ track <TRACK-ID> ] [ bfd ]
- <VRF> – VRF name, set by the string of up to 31 characters.
- <SUBNET> – destination address, can be specified in the following format:
- BBB.CCC.DDD – host IP address, where each part takes values of [0..255].
- BBB.CCC.DDD/NN – network IP address with prefix mask, where AAA-DDD take values of [0..255] and NN takes values of [1..32].
- <NEXTHOP> – gateway IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255];
- <IF> – an IP interface name specified in the form described in Section Types and naming order of router interfaces;
- <TUN> – the name of the tunnel is specified as described in section Types and naming order of router tunnels;
- <RULE> – wan rule number, set in the range of [1..50];
- blackhole – when specifying the command, the packets to this subnet will be removed by the device without sending notifications to a sender;
- unreachable – when specifying the command, the packets to this subnet will be removed by the device, a sender will receive in response ICMP Destination unreachable (Host unreachable, code 1);
- prohibit – when specifying the command, the packets to this subnet will be removed by the device, a sender will receive in response ICMP Destination unreachable (Communication administratively prohibited, code 13);
- bfd – when specifying the given key, the removal of static route in case of next-hop unavailability is activated.
To add static IPv6 route to the given subnet, use the following command:
ipv6 route [ vrf <VRF> ] <SUBNET> { <NEXTHOP> [ resolve ] | interface <IF> | wan load-balance rule <RULE> | blackhole | unreachable | prohibit } [ <METRIC> ] [ bfd ]
- <VRF> – VRF name, set by the string of up to 31 characters.
- <SUBNET> – destination address, can be specified in the following formats:
- The addresses are defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF].
- <IPV6-ADDR/LEN> – IP address and mask of a subnet, defined as X:X:X:X::X/EE where each X part takes values in hexadecimal format [0..FFFF] and EE takes values of [1..128].
- <IPV6-ADDR> – client IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF];
- resolve – when specifying the given parameter, gateway IPv6 address will be recursively calculated through the routing table. If the recursive calculation fails to find a gateway from a directly connected subnet, then this route will not be installed into the system;
- <IF> – an IP interface name specified in the form described in Section Types and naming order of router interfaces;
- blackhole – when specifying the command, the packets to this subnet will be removed by the device without sending notifications to a sender;
- unreachable – when specifying the command, the packets to this subnet will be removed by the device, a sender will receive in response ICMP Destination unreachable (Host unreachable, code 1);
- prohibit – when specifying the command, the packets to this subnet will be removed by the device, a sender will receive in response ICMP Destination unreachable (Communication administratively prohibited, code 13);
- <METRIC> – route metric, takes values of [0..255].
- bfd – when specifying the given key, the removal of static route in case of next-hop unavailability is activated.
Static routes configuration example
Objective:
Configure Internet access for users in LAN 192.168.1.0/24 and 10.0.0.0/8 using the static routing. On R1 device, create gateway for Internet access. Traffic within LAN should be routed within LAN zone, traffic from the Internet should belong to WAN zone.
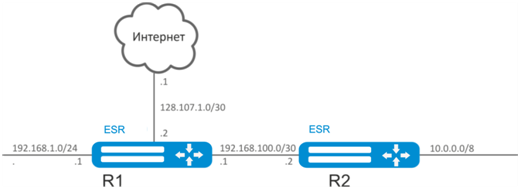
Solution:
Specify the device name for R1 router:
esr# hostname R1Specify 192.168.1.1/24 address and the “LAN” zone for the gi1/0/1 interface. R1 interface will be connected to 192.168.1.0/24 network via this interface:
esr(config)# interface gi1/0/1
esr(config-if-gi)# security-zone LAN
esr(config-if-gi)# ip address 192.168.1.1/24
esr(config-if-gi)# exitSpecify 192.168.100.1/30 address and the 'LAN' zone for the gi1/0/2 interface. R1 will be connected to R2 device via the given interface for the further traffic routing:
esr(config)# interface gi1/0/2
esr(config-if-gi)# security-zone LAN
esr(config-if-gi)# ip address 192.168.100.1/30
esr(config-if-gi)# exitSpecify 128.107.1.2/30 address and the “WAN” zone for the gi1/0/3 interface. R1 interface will be connected to the Internet via this interface:
esr(config)# interface gi1/0/3
esr(config-if-gi)# security-zone WAN
esr(config-if-gi)# ip address 128.107.1.2/30
esr(config-if-gi)# exitCreate a route for interaction with 10.0.0.0/8 network using R2 device as a gateway (192.168.100.2):
esr(config)# ip route 10.0.0.0/8 192.168.100.2 Create a route for interaction with the Internet using the provider gateway as a nexthop (128.107.1.1):
esr(config)# ip route 0.0.0.0/0 128.107.1.1 Specify the device name for R2 router:
esr# hostname R2Specify 10.0.0.1/8 address and the 'LAN' zone for the gi1/0/1 interface. R2 interface will be connected to 10.0.0.0/8 network via this interface:
esr(config)# interface gi1/0/1
esr(config-if-gi)# security-zone LAN
esr(config-if-gi)# ip address 10.0.0.1/8
esr(config-if-gi)# exitSpecify 192.168.100.2/30 address and the 'LAN' zone for the gi1/0/2 interface. R2 will be connected to R1 device via the given interface for the further traffic routing:
esr(config)# interface gi1/0/2
esr(config-if-gi)# security-zone LAN
esr(config-if-gi)# ip address 192.168.100.2/30
esr(config-if-gi)# exitCreate a default route by specifying the IP address of R1 router gi1/0/2 interface (192.168.100.1) as a nexthop:
esr(config)# ip route 0.0.0.0/0 192.168.100.1You can use the following command to check the routing table:
esr# show ip route
RIP Configuration
RIP is a distance-vector dynamic routing protocol that uses hop count as a routing metric. The maximum amount of hops allowed for RIP is 15. By default, each RIP router transmits full routing table into the network every 30 seconds. RIP operates at 3rd level of TCP/IP stack via UDP port 520.
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Configure RIP precedence for the main routing table (optionally). | esr(config)# ip protocols rip preference <VALUE> | <VALUE> – protocol precedence, takes values in the range of [1..255]. Default value: RIP (100). |
2 | Configure RIP routing tables capacity (optionally). | esr(config)# ip protocols rip max-routes <VALUE> | <VALUE> – amount of RIP routes in the routing table, takes values in the range of[ 1..10000]; 10000. |
3 | Create IP subnets lists that will be used for further filtration of advertised and received IP routes. | esr(config)# ip prefix-list <NAME> | <NAME> – name of a subnet list being configured, set by the string of up to 31 characters. |
4 | Permit or deny the prefixes lists. | esr(config-pl)# permit {object-group <OBJ-GROUP-NETWORK-NAME > <ADDR/LEN> | <IPV6-ADDR/LEN> } [ { eq <LEN> | le <LEN> | ge <LEN> [ le <LEN> ] } ] | <OBJ-GROUP-NETWORK-NAME> – IP addresses profile name, set by the string of up to 31 characters; <LEN> – prefix length, takes values of [1..32] in prefix IP lists;
|
esr(config-pl)# deny {object-group <OBJ-GROUP-NETWORK-NAME> <ADDR/LEN> | <IPV6-ADDR/LEN> } [ { eq <LEN> | le <LEN> | ge <LEN> [ le <LEN> ] } | |||
5 | Switch to the RIP process configuration mode. | esr(config)# router rip esr(config-rip)# | |
6 | Enable RIP. | esr(config-rip)# enable | |
7 | Specify RIP authentication algorithm (optionally). | esr(config-rip)# authentication algorithm { cleartext | md5 } |
|
8 | Set the password for neighbour authentication (optionally). | esr(config-rip)# authentication key ascii-text { <CLEAR-TEXT> | encrypted <ENCRYPTED-TEXT> } | <CLEAR-TEXT> – password, set by the string of 8 to 16 characters; <ENCRYPTED-TEXT> – encrypted password of 8 to 16 bytes (from 16 to 32 characters) in hexadecimal format (0xYYYY ...) or (YYYY ...). |
9 | Specify the list of passwords for authentication via md5 hashing algorithm (optionally). | esr(config-rip)# authentication key-chain <KEYCHAIN> | <KEYCHAIN> – key list identifier, set by the string of up to 16 characters. |
10 | Disable routes advertising on the interfaces/tunnels/bridge where it is not necessary (optionally). | esr(config-rip)# passive-interface {<IF> | <TUN> } | <IF> – interface and identifier; <TUN> – tunnel name and number. |
11 | Set time interval after which the advertising is carried out (optionally). | esr(config-rip)# timers update <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 180 seconds. |
12 | Set time interval of route entry correctness without updating (optionally). | esr(config-rip)# timers invalid <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 180 seconds. |
13 | Set time interval after which the route removing is carried out (optionally). | esr(config-rip)# timers flush <TIME> | <TIME> – time in seconds, takes values of [1..65535]. When setting the value, consider the following rule: «timersinvalid + 60». Default value: 240 seconds. |
14 | Enable subnets advertising. | esr(config-rip)# network <ADDR/LEN> | <ADDR/LEN> – subnet address, set in the following format: AAA.BBB.CCC.DDD/NN – network IP address with prefix mask, where AAA-DDD take values of [0..255] and EE takes values of [1..32]. |
15 | Add subnets filtration in incoming or outgoing updates (optionally). | esr(config-rip)# prefix-list <PREFIX-LIST-NAME> { in | out } | <PREFIX-LIST-NAME> – name of a subnet list being configured, set by the string of up to 31 characters.
|
16 | Enable advertising of routes received in an alternative way (optionally). | esr(config-rip)# redistribute static [ route-map <NAME> ] | <NAME> – name of the route map that will be used for advertised static routes filtration and modification, set by the string of up to 31 characters. |
esr(config-rip)# redistribute connected [ route-map <NAME> ] | <NAME> – name of the route map that will be used for filtration and modification of advertised directly connected subnets, set by the string of up to 31 characters. | ||
esr(config-rip)# redistribute ospf <ID><ROUTE-TYPE> [ route-map <NAME> ] | <ID> – process number, takes values of [1..65535]. <ROUTE-TYPE> – route type:
<NAME> – name of the route map that will be used for advertised OSFP routes filtration and modification, set by the string of up to 31 characters. | ||
esr(config-rip)# redistribute bgp <AS> [ route-map <NAME> ] | <AS> – stand alone system number, takes values of [1..4294967295]. <NAME> – name of the route map that will be used for advertised BGP routes filtration and modification, set by the string of up to 31 characters. | ||
17 | Switch to the interface/tunnel/network bridge configuration mode. | esr(config)# interface <IF-TYPE><IF-NUM> | <IF-TYPE> – interface type; <IF-NUM> – F/S/P – F frame (1), S – slot (0), P – port. |
esr(config)# tunnel <TUN-TYPE><TUN-NUM> | <TUN-TYPE> – tunnel type; <TUN-NUM> – tunnel number. | ||
esr(config)# bridge <BR-NUM> | <BR-NUM> – bridge number. | ||
18 | Set RIP routes metric value on the interface (optionally). | esr(config-if-gi)# ip rip metric <VALUE> | <VALUE> – metric size, takes values of [0..32767]. Default value: 5. |
19 | Set the routes advertising mode via RIP (optionally). | esr(config-if-gi)# ip rip mode <MODE> | <MODE> – routes advertising mode:
Default value: multicast. |
20 | Specify a neighbour’s IP address for establishment of a relation in routes advertising unicast mode (optionally). | esr(config-if-gi)# ip rip neighbor <ADDR> | <ADDR> – IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
21 | Enable subnet summarization (optionally). | esr(config-if-gi)# ip rip summary-address <ADDR/LEN> | <ADDR/LEN> – IP address and subnet mask, defined as AAA.BBB.CCC.DDD/EE where each part AAA-DDD takes values of [0..255] and EE takes values of [1..32]. |
RIP configuration example
Objective:
Configure RIP on the router in order to exchange the routing information with neighbouring routers. The router should advertise static routes and subnets 115.0.0.0/24, 14.0.0.0/24, 10.0.0.0/24. Routes should be advertised each 25 seconds.
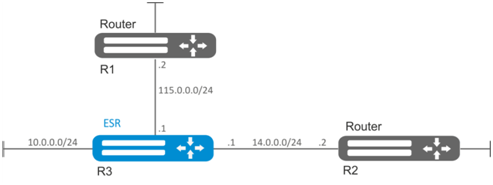
Solution:
Pre-configure IP addresses on interfaces according to the network structure shown in figure.
Switch to the RIP configuration mode:
esr(config)# router rip Specify the networks to be advertised by protocol: 115.0.0.0/24, 14.0.0.0/24 и 10.0.0.0/24:
esr(config-rip)# network 115.0.0.0/24
esr(config-rip)# network 14.0.0.0/24
esr(config-rip)# network 10.0.0.0/24To advertise static routes by the protocol, execute the following command:
esr(config-rip)# redistribute staticConfigure timer, responsible for routing information transmission:
esr(config-rip)# timers update 25When all required settings are done, enable the protocol:
esr(config-rip)# enableTo view the RIP routing table, use the following command:
esr# show ip ripIn addition to RIP protocol configuration, open UDP port 520 in the firewall.
OSFP configuration
OSPF is a dynamic routing protocol, based on link-state technology and using shortest path first Dijkstra algorithm.
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Configure OSFP precedence for the main routing table (optionally). | esr(config)# ip protocols ospf preference <VALUE> | <VALUE> – protocol precedence, takes values in the range of [1..255]. Default value: 150. |
esr(config-vrf)# ip protocols ospf preference <VALUE> | |||
2 | Configure OSFP routing tables capacity (optionally). | esr(config)# ip protocols ospf max-routes <VALUE> | <VALUE> – amount of OSPF routes in the routing table, takes values in the range of:
Default value for the global mode:
Default value for VRF: 0 |
esr(config)# ipv6 protocols ospf max-routes <VALUE> | |||
3 | Enable the output of OSPF neighbor state information (optionally). | esr(config)# router ospf log-adjacency-changes | |
esr(config)# ipv6 router ospf log-adjacency-changes | |||
4 | Create IP subnets lists that will be used for further filtration of advertised and received IP routes. | esr(config)# ip prefix-list <NAME> | <NAME> – name of a subnet list being configured, set by the string of up to 31 characters. |
esr(config)# ipv6 prefix-list <NAME> | |||
5 | Permit or deny the prefixes lists. | esr(config-pl)# permit [ { object-group <OBJ-GROUP-NETWORK-NAME> | <ADDR/LEN> | <IPV6-ADDR/LEN> } ] [ { eq <LEN> | le <LEN> | ge <LEN> [ le <LEN> ] } ] | <OBJ-GROUP-NETWORK-NAME> – IPv4/IPv6 addresses profile name, set by the string of up to 31 characters; <ADDR> – IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]; <LEN> – prefix length, takes values of [1..32] in prefix IP lists;
|
esr(config-pl)# deny [ { object-group <OBJ-GROUP-NETWORK-NAME> | <ADDR/LEN > | <IPV6-ADDR/LEN> } ] [ { eq <LEN> | le <LEN> | ge <LEN> [ le <LEN> ] } ] | |||
6 | Add OSFP process to the system and switch to the OSFP process parameters configuration mode. | esr(config)# router ospf <ID> [vrf <VRF>] | <ID> – stand alone system number, takes values of [1..65535]. <VRF> – VRF instance name, set by the string of up to 31 characters, within which the routing protocol will operate. |
esr(config)# ipv6 router ospf <ID> [vrf <VRF>] | |||
7 | Set the router identifier for the given OSFP process. | esr(config-ospf)# router-id <ID> | <ID> – router identifier, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
esr(config-ipv6-ospf)# router-id <ID> | |||
8 | Define OSFP process routes precedence. | esr(config-ospf)# preference <VALUE> | <VALUE> – OSFP process routes precedence, takes values in the range of [1..255]. Default value: 10. |
esr(config-ipv6-ospf)# preference <VALUE> | |||
9 | Enable compatibility with RFC 1583 (optionally). | esr(config-ospf)# compatible rfc1583 | |
esr(config-ipv6-ospf)# compatible rfc1583 | |||
11 | Add subnets filtration in incoming or outgoing updates (optionally). | esr(config-ospf)# prefix-list <PREFIX-LIST-NAME> { in | out } | <PREFIX-LIST-NAME> – name of a subnet list being configured, set by the string of up to 31 characters.
|
esr(config-ipv6-ospf)# prefix-list <PREFIX-LIST-NAME> { in | out } | |||
12 | Enable advertising of routes received in an alternative way (optionally). | esr(config-ospf)# redistribute static [ route-map <NAME> ] | <NAME> – name of the route map that will be used for advertised static routes filtration and modification, set by the string of up to 31 characters. |
esr(config-ipv6-ospf)# redistribute static [ route-map <NAME> ] | |||
esr(config-ospf)# redistribute connected [ route-map <NAME> ] | <NAME> – name of the route map that will be used for filtration and modification of advertised directly connected subnets, set by the string of up to 31 characters. | ||
esr(config-ipv6-ospf)# redistribute connected [ route-map <NAME> ] | |||
esr(config-ospf)# redistribute rip [ route-map <NAME> ] | <NAME> – name of the route map that will be used for advertised RIP routes filtration and modification, set by the string of up to 31 characters. | ||
esr(config-ospf)# redistribute bgp <AS> [ route-map <NAME> ] | <AS> – stand alone system number, takes values of [1..4294967295]. <NAME> – name of the route map that will be used for advertised BGP routes filtration and modification, set by the string of up to 31 characters. | ||
esr(config-ipv6-ospf)# redistribute bgp <AS> [ route-map <NAME> ] | |||
13 | Enable OSFP process. | esr(config-ospf)# enable | |
esr(config-ipv6-ospf)# enable | |||
14 | Create OSFP area and switch to the scope configuration mode. | esr(config-ospf)# area <AREA_ID> | <AREA_ID> – area identifier, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
esr(config-ipv6-ospf)# area <AREA_ID> | |||
15 | Enable subnets advertising. | esr(config-ospf-area)# network <ADDR/LEN> | <ADDR/LEN> – subnet address, set in the following format: AAA.BBB.CCC.DDD/NN – network IP address with prefix mask, where AAA-DDD take values of [0..255] and EE takes values of [1..32]. |
esr(config-ipv6-ospf-area)# network <IPV6-ADDR/LEN> | <IPV6-ADDR/LEN> – IPv6 address and mask of a subnet, defined as X:X:X:X::X/EE where each X part takes values in hexadecimal format [0..FFFF] and EE takes values of [1..128]. | ||
16 | Specify the area type | esr(config-ospf-area)# area-type <TYPE> [ no-summary ] | <TYPE> – area type:
|
esr(config-ipv6-ospf-area)# area-type <TYPE> [ no-summary ] | |||
17 | Enable the default route generation for NSSA area and its advertising as NSSA-LSA. | esr(config-ospf-area)# default-information-originate | |
esr(config-ipv6-ospf-area)# default-information-originate | |||
18 | Enable the subnet summarization or hiding. | esr(config-ospf-area)# summary-address <ADDR/LEN> { advertise | not-advertise } | <ADDR/LEN> – IP address and subnet mask, defined as AAA.BBB.CCC.DDD/EE where each part AAA-DDD takes values of [0..255] and EE takes values of [1..32];
|
esr(config-ipv6-ospf-area)# summary-address <IPV6-ADDR/LEN> { advertise | not-advertise } | <IPV6-ADDR/LEN> – IPv6 address and mask of a subnet, defined as X:X:X:X::X/EE where each X part takes values in hexadecimal format [0..FFFF] and EE takes values of [1..128];
| ||
19 | Enable OSFP area. | esr(config-ospf-area)# enable | |
esr(config-ipv6-ospf-area)# enable | |||
20 | Establish a virtual connection between the main and remote areas having several areas between them. | esr(config-ospf-area)# virtual-link <ID> | <ID> – identifier of the router with which the virtual connection is established, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
esr(config-ipv6-ospf-area)# virtual-link <ID> | |||
21 | Set the time interval in seconds after which the router re-sends a packet that has not received a delivery confirmation (for example, a DatabaseDescription packet or LinkStateRequest packets). | esr(config-ospf- vlink)# restransmit-interval <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 5 seconds. |
esr(config-ipv6-ospf- vlink)# restransmit-interval <TIME> | |||
22 | Set the time interval in seconds after which the router sends the next hello packet. | esr(config-ospf- vlink)# hello-interval <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 10 seconds. |
esr(config-ipv6-ospf- vlink)# hello-interval <TIME> | |||
23 | Set the time interval in seconds after which the neighbor is considered to be idle. This interval should be a multiple of the ‘hello interval’ value. | esr(config-ospf- vlink)# dead-interval <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 40 seconds. |
esr(config-ipv6-ospf- vlink)# dead-interval <TIME> | |||
24 | Set the time interval in seconds after which the router selects DR in the network. | esr(config-ospf- vlink)# wait-interval <TIME> | <TIME> – time in seconds, takes values of [1..65535]. |
esr(config-ipv6-ospf- vlink)# wait-interval <TIME> | |||
25 | Define authentication algorithm. | esr(config-ospf- vlink)# authentication algorithm <ALGORITHM> | <ALGORITHM> – authentication algorithm:
|
26 | Set the password for neighbour authentication. | esr(config-ospf- vlink)# authentication key ascii-text { <CLEAR-TEXT> | encrypted <ENCRYPTED-TEXT> } | <CLEAR-TEXT> – password, set by the string of 8 to 16 characters. <ENCRYPTED-TEXT> – encrypted password of 8 to 16 bytes (from 16 to 32 characters) in hexadecimal format (0xYYYY ...) or (YYYY ...). |
27 | Specify the list of passwords for authentication via md5 hashing algorithm. | esr(config-ospf- vlink)# authentication key chain <KEYCHAIN> | <KEYCHAIN> – key list identifier, set by the string of up to 16 characters. |
28 | Enable virtual connection. | esr(config-ospf- vlink)# enable | |
29 | Switch to the interface/tunnel/network bridge configuration mode. | esr(config)# interface <IF-TYPE><IF-NUM> | <IF-TYPE> – interface type; <IF-NUM> – F/S/P – F frame (1), S – slot (0), P – port. |
esr(config)# tunnel <TUN-TYPE><TUN-NUM> | <TUN-TYPE> – tunnel type; <TUN-NUM> – tunnel number. | ||
esr(config)# bridge <BR-NUM> | <BR-NUM> – bridge number. | ||
30 | Define the interface / tunnel / network bridge inherence to a specific OSPF process. | esr(config-if-gi)# ip ospf instance <ID> | <ID> – process number, takes values of [1..65535]. |
esr(config-if-gi)# ipv6 ospf instance <ID> | |||
31 | Define the interface inherence to a specific OSPF process area. | esr(config-if-gi)# ip ospf area <AREA_ID> | <AREA_ID> – area identifier, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
esr(config-if-gi)# ipv6 ospf area <AREA_ID> | |||
32 | Enable the routing via OSFP on the interface. | esr(config-if-gi)# ip ospf | |
esr(config-if-gi)# ipv6 ospf | |||
33 | Enable the mode in which the OSPF process will ignore MTU interface value in incoming Database Description packets. | esr(config-if-gi)# ip ospf mtu-ignore | |
esr(config-if-gi)# ipv6 ospf mtu-ignore | |||
34 | Specify OSFP authentication algorithm. | esr(config-if-gi)# ip ospf authentication algorithm <ALGORITHM> | <ALGORITHM> – authentication algorithm:
|
35 | Set the password for OSPF neighbor authentication when transmitting an unencrypted password. | esr(config-if-gi)# ip ospf authentication key ascii-text { <CLEAR-TEXT> | encrypted <ENCRYPTED-TEXT> } | <CLEAR-TEXT> – password, set by the string of 8 to 16 characters; <ENCRYPTED-TEXT> – encrypted password of 8 to 16 bytes (from 16 to 32 characters) in hexadecimal format (0xYYYY ...) or (YYYY ...). |
36 | Specify the list of passwords for neighbor authentication via md5 hashing algorithm. | esr(config-if-gi)# ip ospf authentication key-chain <KEYCHAIN> | <KEYCHAIN> – key list identifier, set by the string of up to 16 characters. |
37 | Set the time interval in seconds after which the router selects DR in the network. | esr(config-if-gi)# ip ospf wait-interval <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 40 seconds. |
esr(config-if-gi)# ipv6 ospf wait-interval <TIME> | |||
38 | Set the time interval in seconds after which the router re-sends a packet that has not received a delivery confirmation (for example, a DatabaseDescription packet or LinkStateRequest packets). | esr(config-if-gi)# ip ospf restransmit-interval <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 5 seconds. |
esr(config-if-gi)# ipv6 ospf restransmit-interval <TIME> | |||
39 | Set the time interval in seconds after which the router sends the next hello packet. | esr(config-if-gi)# ip ospf hello-interval <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 10 seconds. |
esr(config-if-gi)# ipv6 ospf hello-interval <TIME> | |||
40 | Set the time interval in seconds after which the neighbor is considered to be idle. This interval should be a multiple of the ‘hello interval’ value. | esr(config-if-gi)# ip dead-interval <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 40 seconds. |
esr(config-if-gi)# ipv6 dead-interval <TIME> | |||
41 | Set the time interval during which NBMA interface waits before sending a HELLO packet to a neighbor, even if the neighbor is idle. | esr(config-if-gi)# ip poll-interval <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 120 seconds. |
esr(config-if-gi)# ipv6 poll-interval <TIME> | |||
42 | Set static IP address of a neighbor to establish a relation in NMBA and P2MP (Point-to-MultiPoint) networks. | esr(config-if-gi)# ip ospf neighbor <IP> [ eligible ] | <IP> – neighbor’s IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. eligible – optional parameter, allows the device to take part in DR selection process in NMBA networks. The interface priority should be greater than zero. |
esr(config-if-gi)# ip ospf neighbor <IP> [ eligible ] | <IPV6-ADDR> – neighbor’s IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]; eligible – optional parameter, allows the device to take part in DR selection process in NMBA networks. The interface priority should be greater than zero. | ||
43 | Define the network type for OSPF neighborhood establishment. | esr(config-if-gi)# ip ospf network <TYPE> | <TYPE> – network type:
Default value: broadcast. |
esr(config-if-gi)# ipv6 ospf network <TYPE> | |||
44 | Set the router priority that is used for DR and BDR selection. | esr(config-if-gi)# ip ospf priority <VALUE> | <VALUE> – interface priority, takes values of [1..65535]. Default value: 120. |
esr(config-if-gi)# ipv6 ospf priority <VALUE> | |||
45 | Set the metric size on the interface or tunnel. | esr(config-if-gi)# ip ospf cost <VALUE> | <VALUE> – metric size, takes values of [0..32767]. Default value: 150. |
esr(config-if-gi)# ipv6 ospf cost <VALUE> | |||
47 | Enable BFD protocol for OSPF protocol. | esr(config-if-gi)# ip ospf bfd-enable | |
esr(config-if-gi)# ipv6 ospf bfd-enable |
OSPF configuration example
Objective:
Configure OSPF protocol on the router in order to exchange the routing information with neighbouring routers. The router should be in 1.1.1.1 identifier area and announce routes received via RIP.
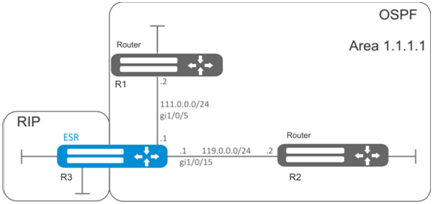
Solution:
Pre-configure IP addresses on interfaces according to the network structure shown in figure.
Create OSPF process with identifier 10 and proceed to the OSPF protocol configuration mode:
esr(config)# router ospf 10Create and enable the required area:
esr(config-ospf)# area 1.1.1.1
esr(config-ospf-area)# enable
esr(config-ospf-area)# exitEnable advertising of the routing information from RIP:
esr(config-ospf)# redistribute ripEnable OSFP process:
esr(config-ospf)# enable
esr(config-ospf)# exitNeighbouring routers are connected to gi1/0/5 and gi1/0/15 interfaces. To establish the neighbouring with other routers, map them to OSPF process and the area. Next, enable OSPF routing for the interface.
esr(config)# interface gigabitethernet 1/0/5
esr(config-if-gi)# ip ospf instance 10
esr(config-if-gi)# ip ospf area 1.1.1.1
esr(config-if-gi)# ip ospf
esr(config-if-gi)# exitesr(config)# interface gigabitethernet 1/0/15
esr(config-if-gi)# ip ospf instance 10
esr(config-if-gi)# ip ospf area 1.1.1.1
esr(config-if-gi)# ip ospf
esr(config-if-gi)# exit
esr(config)# exitOSPF stub area configuration example
Objective:
Change 1.1.1.1 area type, area should be stub. Stub router should advertise routes received via RIP.
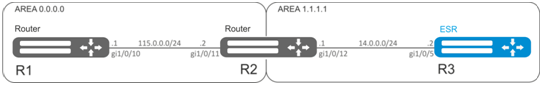
Solution:
Pre-configure OSPF protocol and IP addresses on interfaces according to the network structure shown in figure.
Change area type to stub. For each router from 1.1.1.1 area, execute the following command in the configuration mode:
esr(config-ospf-area)# area-type stubFor R3 stub router, enable advertising of the routing information from RIP:
esr(config-ospf)# redistribute ripVirtual link configuration example
Objective:
Merge two backbone areas using virtual link.
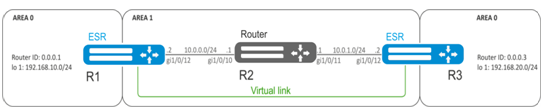
Solution:
Virtual link is a specialized connection that allows you to merge a split zone or connect a zone to the backbone zone trough the third zone. Virtual link is configured between two Area Border Routers (ABR).
Pre-configure OSPF protocol and IP addresses on interfaces according to the network structure shown in figure.
For R1 router, proceed to 1.1.1.1 area configuration mode:
esr(config-ospf)# area 1.1.1.1Create and enable virtual link with the identifier 0.0.0.3:
esr(config-ospf-area)# virtual-link 0.0.0.3
esr(config-ospf-vlink)# enableFor R3 router, proceed to 1.1.1.1 area configuration mode:
esr(config-ospf)# area 1.1.1.1Create and enable virtual link with the identifier 0.0.0.1:
esr(config-ospf-area)# virtual-link 0.0.0.1
esr(config-ospf-vlink)# enableConsider the routing table on R1 router:
esr# show ip route
C * 10.0.0.0/24 [0/0] dev gi1/0/12, [direct 00:49:34]
O * 10.0.1.0/24 [150/20] via 10.0.0.1 on gi1/0/12, [ospf1 00:49:53] (0.0.0.3)
O * 192.168.20.0/24 [150/30] via 10.0.0.1 on gi1/0/12, [ospf1 00:50:15] (0.0.0.3)
C * 192.168.10.0/24 [0/0] dev lo1, [direct 21:32:01]Review the routing table on R3 router:
esr# show ip route
O * 10.0.0.0/24 [150/20] via 10.0.1.1 on gi1/0/12, [ospf1 14:38:35] (0.0.0.2)
C * 10.0.1.0/24 [0/0] dev gi1/0/12, [direct 14:35:34]
C * 192.168.20.0/24 [0/0] dev lo1, [direct 14:32:58]
O * 192.168.10.0/24 [150/30] via 10.0.1.1 on gi1/0/12, [ospf1 14:39:54] (0.0.0.1)Since OSPF considers virtual link as the part of the area, R1 routes received from R3 are marked as an intrazone and vice versa.
To view the neighbors, use the following command:
esr# show ip ospf neighbors 10To view OSPF routing table, use the following command:
esr# show ip ospf 10In the firewall, you should enable OSPF protocol (89).
BGP configuration
BGP protocol is designed to exchange subnet reachability information among autonomous systems (AS), i.e. router groups united under a single technical control that uses interdomain routing protocol for defining packet delivery routes to other AS. Transmitted information includes a list of AS that are accessible through this system. Selection of the optimal routes is based on effective rules for the network.
Configuration algorithm
To establish a BGP session it is necessary to allow TCP port 179 on the firewall.
Step | Description | Command | Keys |
|---|---|---|---|
1 | Configure BGP precedence for the main routing table (optional). | esr(config)# ip protocols bgp preference <VALUE> | <VALUE> – protocol precedence, takes values in the range of [1..255]. Default value: BGP (170). |
2 | Configure the BGP routing table capacity (not required when using the global routing table). | esr(config)# ip protocols bgp max-routes <VALUE> | <VALUE> – amount of BGP routes in the routing table, takes values in the range of:
The default value for the global routing table:
Default value for VRF: 0. |
esr(config)# ipv6 protocols bgp max-routes <VALUE> | |||
esr(config-vrf)# ip protocols bgp max-routes <VALUE> | |||
esr(config-vrf)# ipv6 protocols bgp max-routes <VALUE> | |||
3 | Enable the output of BGP neighbor state information (optional). | esr(config)# router bgp log-neighbor-changes | |
esr(config)# ipv6 router bgp log-neighbor-changes | |||
4 | Enable ECMP and define the maximum amount of equal routes to a destination point. | esr(config)# router bgp maximum-paths <VALUE> | <VALUE> – amount of valid equal routes to the target, takes the values of [1..16]. |
3 | Select the filtering method for the information transmitted between routers. (Mandatory when configuring eBGP to announce subnets) | ||
3.1.1 | If you select the route-map-based filtering method, create a list of rules that will be used to filter the advertised and received IP routes in the future. | esr(config)# route-map <NAME> | <NAME> – configured routing rule name, set by the string of up to 31 characters. |
3.1.2 | Create rule | (config-route-map)# rule <ORDER> | <ORDER> – rule number, takes values of [1..10000]. |
3.1.3 | Define the list of subnets affected by the rule. | esr(config-route-map-rule)#match ip address { <ADDR/LEN> | object-group <OBJ-GRP-NETNAME> } [ { eq <LEN> | le <LEN> | ge <LEN 1> [ le <LEN 2> ] } ] | <ADDR/LEN> – IP address and subnet mask, in the format of. AAA.BBB.CCC.DDD/EE – network IP address with prefix mask, where AAA-DDD take values of [0..255] and EE takes values of [1..32]; <IPV6-ADDR/LEN> – IPv6 address and subnet mask, in the format of: X:X:X:X::X/EE, where each X part takes values in hexadecimal format [0..FFFF] and EE takes values of [1..128]; <OBJ-GRP-NETNAME> – IP addresses profile name, set by the string of up to 31 characters*; <LEN>, <LEN 1>, <LEN 2> – prefix length, may take values [1..32] in prefix IP lists for IPv4 and [1..128] for IPv6; eq – when specifying the command, the prefix length mast match the specified one; le – when specifying the command, the prefix length mast be less than or match the specified one; ge – when specifying the command, the prefix length mast be more than or match the specified one; ge <LEN 1> le <LEN 2> – When specifying a command, the prefix length must be greater than or equal to <LEN> but less than or equal to <LEN1>. * When using object-group filtering, they must be created in advance. |
esr(config-route-map-rule)#match ipv6 address { <IPV6-ADDR/LEN> | object-group <OBJ-GRP-NETNAME> } [ { eq <LEN> | le <LEN> | ge <LEN 1> [ le <LEN 2> ] } ] | |||
3.1.4 | Permit or deny action for the specified subnets in the rule. | esr(config-route-map-rule)# action {deny | permit} | |
3.2.1 | If you select the prefix-list-based filtering method, create a list of IP networks that will be used to filter the advertised and received IP routes in the future. | esr(config)# ip prefix-list <NAME> | <NAME> – name of a subnet list being configured, set by the string of up to 31 characters. |
esr(config)# ipv6 prefix-list <NAME> | |||
3.2.2 | Permit or deny the prefixes lists. | esr(config-pl)# permit { <ADDR/LEN> | object-group <OBJ-GRP-NETNAME>} [ { eq <LEN> | le <LEN> | ge <LEN 1> [ le <LEN 2> ] } ] | <ADDR/LEN> – IP address and subnet mask, in the format of. AAA.BBB.CCC.DDD/EE – network IP address with prefix mask, where AAA-DDD take values of [0..255] and EE takes values of [1..32]; <IPV6-ADDR/LEN> – IPv6 address and subnet mask, in the format of: X:X:X:X::X/EE, where each X part takes values in hexadecimal format [0..FFFF] and EE takes values of [1..128]; <OBJ-GRP-NETNAME> – IP addresses profile name, set by the string of up to 31 characters*; <LEN>, <LEN 1>, <LEN 2> – prefix length, may take values [1..32] in prefix IP lists for IPv4 and [1..128] for IPv6; eq – when specifying the command, the prefix length mast match the specified one; le – when specifying the command, the prefix length mast be less than or match the specified one; ge – when specifying the command, the prefix length mast be more than or match the specified one; ge <LEN 1> le <LEN 2> – When specifying a command, the prefix length must be greater than or equal to <LEN> but less than or equal to <LEN1>. * When using object-group filtering, they must be created in advance. |
esr(config-pl)# deny {<ADDR/LEN> | object-group <OBJ-GRP-NETNAME>} [ { eq <LEN> | le <LEN> | ge <LEN 1> [ le <LEN 2> ] } ] | |||
esr(config-ipv6-pl)# permit { <IPV6-ADDR/LEN> | object-group <OBJ-GRP-NETNAME>} [ { eq <LEN> | le <LEN> | ge <LEN 1> [ le <LEN 2> ] } ] | |||
esr(config-ipv6-pl)# deny {<IPV6-ADDR/LEN> | object-group <OBJ-GRP-NETNAME> } [ { eq <LEN> | le <LEN> | ge <LEN 1> [ le <LEN 2> ] } ] | |||
4 | Add BGP process to the system and switch to the BGP process parameters configuration mode. | esr(config)# router bgp <AS> | <AS> – stand alone system number, takes values of [1..4294967295]. |
5 | Set the router identifier. | esr(config-bgp)# router-id <ID> | <ID> – router identifier, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
6 | Set the Route-Reflector identifier of the cluster to which the router BGP process belongs. (If necessary) | esr(config-bgp)# cluster-id <ID> | <ID> – Route-Reflector cluster identifier, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
7 | Enable generation and sending of a default route, if the default route is in the FIB routing table. (optionally) | esr(config-bgp)# default-information-originate | |
8 | Set the time interval after which the connection with the opposing party is checked. (Optional) | esr(config-bgp-af)# timers keepalive <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 60 seconds. |
9 | Set time interval after which the opposing party is considered to be unavailable. (Optional) | esr(config-bgp-af)# timers holdtime <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 180 seconds. |
10 | Set the time of minimum and maximum delay during which it is prohibited to establish a connection in order to prevent frequent disconnections (Optional) | esr(config-bgp-af)# timers error-wait <TIME1> <TIME2> | <TIME1> – minimum delay time in seconds, takes values of [1..65535]. <TIME2> – maximum delay time in seconds, takes values of [1..65535]. |
11 | Define the global algorithm of neighbor authentication (if necessary). | esr(config-bgp)# authentication algorithm <ALGORITHM> | <ALGORITHM> – encryption algorithm: · md5 – password is encrypted by md5 algorithm. Default value: Encryption is not used |
12 | Set a global password for authentication with neighbors. (Used in conjunction with «authentication algorithm») | esr(config-bgp)# authentication key ascii-text { <CLEAR-TEXT> | encrypted <ENCRYPTED-TEXT> } | <CLEAR-TEXT> – password, set by the string of 8 to 16 characters; <ENCRYPTED-TEXT> – encrypted password of 8 to 16 bytes (from 16 to 32 characters) in hexadecimal format (0xYYYY ...) or (YYYY ...). |
13 | Enable BGP process. | esr(config-bgp)# enable | |
14 | Define the type of configured routing information and switch to this configuration mode. | esr(config-bgp)# address-family { ipv4 | ipv6 } unicast | ipv 4 – IPv4 family; ipv 6 – IPv6 family; |
15 | Enable route advertising by BGP process obtained alternatively (if necessary). | esr(config-bgp-af)# redistribute static [ route-map <NAME> ] | <NAME> – name of the route map that will be used for advertised static routes filtration and modification, set by the string of up to 31 characters. |
esr(config-bgp-af)# redistribute connected [ route-map <NAME> ] | <NAME> – name of the route map that will be used for filtration and modification of advertised directly connected subnets, set by the string of up to 31 characters. | ||
esr(config-bgp-af)# redistribute rip [ route-map <NAME> ] | <NAME> – name of the route map that will be used for advertised RIP routes filtration and modification, set by the string of up to 31 characters. | ||
esr(config-bgp-af)# redistribute ospf <ID> <ROUTE-TYPE 1> [<ROUTE-TYPE 2>] [<ROUTE-TYPE 3>] [<ROUTE-TYPE 4>] [ route-map <NAME> ] | <ID> – process number, takes values of {1..65535}; <ROUTE-TYPE> – route type:
<NAME> – name of the route map that will be used for advertised OSFP routes filtration and modification, set by the string of up to 31 characters. | ||
esr(config-bgp-af)# redistribute bgp <AS> [ route-map <NAME> ] | <AS> – stand alone system number, takes values of [1..4294967295]. <NAME> – name of the route map that will be used for advertised BGP routes filtration and modification, set by the string of up to 31 characters. | ||
16 | Enable subnets advertising. | esr(config-bgp-af)# network <ADDR/LEN> | <ADDR/LEN> – subnet address, set in one of the following formats:
|
17 | Exit global BGP process route information advertisement configuration mode | esr(config-bgp-af)# exit | |
18 | Add BGP neighbor and switch to the BGP process parameters configuration mode. | esr(config-bgp)# neighbor <ADDR>|<IPV6-ADDR> | <ADDR> – neighbor’s IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]; <IPV6-ADDR> – client IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]. |
19 | Specify neighbor description (optionally). | esr(config-bgp-neighbor)# description <DESCRIPTION> | <DESCRIPTION> – neighbor description, set by the string of up to 255 characters. |
20 | Set the time interval after which the connection with the opposing party is checked. | esr(config-bgp-neighbor)# timers keepalive <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 60 seconds. |
21 | Set time interval after which the opposing party is considered to be unavailable (optionally). | esr(config-bgp- neighbor)# timers holdtime <TIME> | <TIME> – time in seconds, takes values of [1..65535]. Default value: 180 seconds. |
22 | Set the time of minimum and maximum delay during which it is prohibited to establish a connection in order to prevent frequent disconnections (optionally). | esr(config-bgp-af)# timers error-wait <TIME1> <TIME2> | <TIME1> – minimum delay time in seconds, takes values of [1..65535]. <TIME2> – maximum delay time in seconds, takes values of [1..65535]. Default value: 60 and 300 seconds |
23 | Set the number of BGP neighbor stand alone system. | esr(config-bgp-neighbor)# remote-as <AS> | <AS> – stand alone system number, takes values of [1..4294967295]. |
24 | Allow connections to neighbors that are located not in directly connected subnets (optional) | esr(config-bgp-neighbor)# ebgp-multihop <NUM> | <NUM> – maximum amount of hops when installing EBGP (used for TTL). |
25 | Specify BGP neighbor as a Route-Reflector client. (optional) | esr(config-bgp-neighbor)# route-reflector-client | |
26 | Set IP/IPv6 router address that will be used as source IP/IPv6 address in transmitted BGP route information updates. (optionally) | esr(config-bgp-neighbor)# update-source { <ADDR> | <IPV6-ADDR> } | <ADDR> – source IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]; <IPV6-ADDR> – source IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]. |
27 | Enable the mode in which the reception of routes in the BGP attribute, AS Path of which includes the numbers of process stand alone system, is allowed. (optionally) | esr(config-bgp-neighbor)# allow-local-as <NUMBER> | <NUMBER> – threshold amount of instances of autonomous system number in the AS Path attribute at which the route will be accepted, the range of acceptable values [1..10]. |
28 | Enable the BFD protocol on the configured BGP neighbor. (optional, used in conjunction with the update-source parameter) | esr(config-bgp-neighbor)# bfd-enable | |
29 | Specify neighbor authentication algorithm (optionally). | esr(config-bgp-neighbor)# authentication algorithm <ALGORITHM> | <ALGORITHM> – encryption algorithm: md5 – password is encrypted by md5 algorithm. |
30 | Set the password for neighbour authentication (optionally). | esr(config-bgp-neighbor)# authentication key ascii-text { <CLEAR-TEXT> | encrypted <ENCRYPTED-TEXT> } | <CLEAR-TEXT> – password, set by the string of 8 to 16 characters; <ENCRYPTED-TEXT> – encrypted password of 8 to 16 bytes (from 16 to 32 characters) in hexadecimal format (0xYYYY ...) or (YYYY ...). |
31 | Make neighborhood active | esr(config-bgp-neighbor)# enable | |
32 | Define the type of neighbor configured routing information and switch to this configuration mode. | esr(config-bgp-neighbor)# address-family { ipv4 | ipv6 | vpnv4 } unicast | ipv 4 – IPv4 family; ipv 6 – IPv6 family; vpnv4 – VPNv4 family; |
33 | If prefix list filtering mode is selected, add subnet filtering in incoming or outgoing updates ( Mandatory when configuring eBGP for subnet advertisement). | esr(config-bgp-neighbor-af)# prefix-list <PREFIX-LIST-NAME> { in | out } | <PREFIX-LIST-NAME> – name of a subnet list being configured, set by the string of up to 31 characters. in – incoming routes filtering; out – outgoing routes filtering. |
34 | Set the mode in which the default route is always sent to the BGP neighbor in the update along with other routes. (optional, none for vpnv4) | esr(config-bgp-neighbor-af)# default-originate | |
35 | Set the mode in which all updates are sent to BGP neighbor with the IP address of a local router outgoing interface as the next-hop. | esr(config-bgp-neighbor-af)# next-hop-self | |
36 | Define the precedence of the routes received from a neighbor. (optional) | esr(config-bgp-neighbor-af)# preference <VALUE> | <VALUE> – neighbor routes precedence, takes values in the range of [1..255]. Default value: 170. |
37 | Set the mode in which private numbers of autonomous systems are removed from the AS Path routes BGP attribute before sending an update (in accordance with RFC 6996). (optional, none for vpnv4) | esr(config-bgp-neighbor-af)# remove-private-as [ { all | nearest | replace } ] | all – remove all private AS number from AS-path; nearest – replace the nearest private AS in the AS-path with a nearby public AS; replace – replace all private AS numbers with the number of the current BGP process. Default value: all. |
38 | Enable routing information exchange | esr(config-bgp-neighbor-af)# enable |
It often happens, especially when configuring iBGP, that in one bgp process you need to configure several bgp neighbor with the same parameters. To avoid configuration redundancy, it is recommended to use bgp peer-group in which you can describe common parameters and it is easy to identify the bgp peer-group membership in the bgp neighbor configuration.
Configuration example
Objective:
Configure BGP on the R3 router with the following parameters:
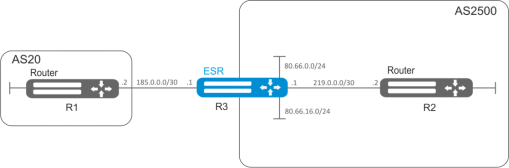
- own subnets: 80.66.0.0/24, 80.66.16.0/24;
- advertising of directly connected subnets;
- proprietary AS 2500;
- first neighbouring – subnet 219.0.0.0/30, proprietary IP address 219.0.0.1, neighbour IP address 219.0.0.2, AS2500;
- second neighbouring – subnet 185.0.0.0/30, proprietary IP address 185.0.0.1, neighbour IP address 185.0.0.2, AS20.
Solution:
Configure required network interfaces:
esr-R3(config)# interface gigabitethernet 1/0/1
esr-R3(config-if-gi)# ip address 185.0.0.1/30
esr-R3(config-if-gi)# exit
esr-R3(config)# interface gigabitethernet 1/0/2
esr-R3(config-if-gi)# ip address 219.0.0.1/30
esr-R3(config-if-gi)# exit
esr-R3(config)# interface gigabitethernet 1/0/3
esr-R3(config-if-gi)# ip address 80.66.0.1/24
esr-R3(config-if-gi)# exit
esr-R3(config)# interface gigabitethernet 1/0/4
esr-R3(config-if-gi)# ip address 80.66.16.1/24
esr-R3(config-if-gi)# exitConfigure the firewall to receive BGP traffic from the WAN security zone:
esr-R3(config)# object-group service og_bgp
esr-R3(config-object-group-service)# port-range 179
esr-R3(config-object-group-service)# exit
esr-R3(config)# security zone wan
esr-R3(config-zone)# exit
esr-R3(config)# security zone-pair wan self
esr-R3(config-zone-pair)# rule 100
esr-R3(config-zone-pair-rule)# match protocol tcp
esr-R3(config-zone-pair-rule)# match destination-port og_bgp
esr-R3(config-zone-pair-rule)# action permit
esr-R3(config-zone-pair-rule)# enable
esr-R3(config-zone-pair-rule)# exit
esr-R3(config-zone-pair)# exitSpecify that the interfaces belong to the security zone:
esr-R3(config)# interface gigabitethernet 1/0/1
esr-R3(config-if-gi)# security-zone wan
esr-R3(config-if-gi)# exit
esr-R3(config)# interface gigabitethernet 1/0/2
esr-R3(config-if-gi)# security-zone wan
esr-R3(config-if-gi)# exitCreate a route-map, which will be used later when configuring enabling advertising to routers from another AS.
esr-R3(config)# route-map bgp-general
esr-R3(config-route-map)# rule 1
esr-R3(config-route-map-rule)# match ip address 80.66.0.0/24
esr-R3(config-route-map-rule)# match ip address 80.66.16.0/24
esr-R3(config-route-map-rule)# action permit
esr-R3(config-route-map-rule)# exit
esr-R3(config-route-map)# exitCreate BGP process for AS 2500 and enter process parameters' configuration mode:
esr(config)# router bgp 2500Configure advertising of directly connected subnets:
esr-R3(config-bgp)# address-family ipv4 unicast
esr-R3(config-bgp-af)# redistribute connected
esr-R3(config-bgp-af)# exitCreate a neighborhood with the R2 router via iBGP:
esr-R3(config-bgp)# neighbor 219.0.0.2
esr-R3(config-bgp-neighbor)# remote-as 2500
esr-R3(config-bgp-neighbor)# enableEnable IPv4 route exchange:
esr-R3(config-bgp-neighbor)# address-family ipv4 unicast
esr-R3(config-bgp-neighbor-af)# enable
esr-R3(config-bgp-neighbor-af)# exit
esr-R3(config-bgp-neighbor)# exitCreate a neighborhood with the R1 router via eBGP:
esr-R3(config-bgp)# neighbor 185.0.0.2
esr-R3(config-bgp-neighbor)# remote-as 20
esr-R3(config-bgp-neighbor)# enableEnable the exchange of ipv4 routes, permitting the necessary routes for advertising by means of a previously prepared route-map:
esr-R3(config-bgp-neighbor)# address-family ipv4 unicast
esr-R3(config-bgp-neighbor-af)# route-map bgp-general out
esr-R3(config-bgp-neighbor-af)# enable
esr-R3(config-bgp-neighbor-af)# exit
esr-R3(config-bgp-neighbor)# exitEnable protocol operation:
esr-R3(config-bgp)# enable
esr-R3(config-bgp)# exitTo view BGP peers information, use the following command:
esr# show ip bgp 2500 neighbors To view BGP routing table, use the following command:
esr# show ip bgpBFD configuration
BFD (Bidirectional Forwarding Detection) is a protocol operating over other protocols and allowing to reduce the problem detection time to 50 msec. BFD is two-party protocol, it requires the configuration of both routers (both routers generate BFD packets and respond to each other).
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Enable BFD for OSFP on the interface | esr(config-if-gi)# ip ospf bfd-enable | |
2 | Enable BFD for BGP neighbor on the interface | esr(config-bgp-neighbor)# bfd-enable | |
3 | Set the interval after which the BFD message is sent to the neighbor. Globally | esr(config)# ip bfd idle-tx-interval <TIMEOUT> | <TIMEOUT> – interval after which the BFD packet should be sent, takes values in milliseconds in the range of [200..65535] for ESR-1000/1200/1500/1511 By default, 1 second |
4 | Enable the logging of BFD protocol state changes (optionally) | esr(config)# ip bfd log-adjacency-changes | |
5 | Set the minimum interval after which the neighbor should generate BFD message. | esr(config)# ip bfd min-rx-interval <TIMEOUT> | <TIMEOUT> – interval after which the BFD message should be sent by the neighbor, takes values in milliseconds in the range of [200..65535] for ESR-1000/1200/1500/1511 By default:
|
6 | Set the minimum interval after which the BFD message is sent to the neighbor. | esr(config)# ip bfd min-tx-interval <TIMEOUT> | <TIMEOUT> – interval after which the BFD message should be sent by the neighbor, takes values in milliseconds in the range of [200..65535] for ESR-1000/1200/1500/1511 By default:
|
7 | Set the amount of dropped packets, at which the BFD neighbor is considered to be unavailable. Globally | esr(config)# ip bfd multiplier <COUNT> | <COUNT> – amount of dropped packets, at which the neighbor is considered to be unavailable, takes values in the range of [1..100]. Default: 5 |
8 | Put BFD mechanism with the specified IP address into operation. | esr(config)# ip bfd neighbor <ADDR> [ { interface <IF> | tunnel <TUN> } ] | <ADDR> – gateway IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]; <IF> – interface or interface group; <TUN> – tunnel type and number. <VRF> – VRF name, set by the string of up to 31 characters. multihop – key for setting TTL=255, for BFD mechanism operation through the routed network. |
9 | Switch BFD session to the passive mode, so that BFD messages will not be sent until the messages from BFD neighbor are received. Globally (optional) | esr(config)# ip bfd passive | |
10 | Set the interval after which the BFD message is sent to the neighbor. | esr(config-if-gi)# ip bfd idle-tx-interval <TIMEOUT> | <TIMEOUT> – interval after which the BFD packet should be sent, takes values in milliseconds in the range of [200..65535] for ESR-1000/1200/1500/1511 Default: 1 second |
11 | Set the minimum interval after which the neighbor should generate BFD message. | esr(config-if-gi)# ip bfd min-rx-interval <TIMEOUT> | <TIMEOUT> – interval after which the BFD message should be sent by the neighbor, takes values in milliseconds in the range of [200..65535] for ESR-1000/1200/1500/1511 By default:
|
12 | Set the minimum interval after which the BFD message is sent to the neighbor. | esr(config-if-gi)# ip bfd min-tx-interval <TIMEOUT> | <TIMEOUT> – interval after which the BFD message should be sent by the neighbor, takes values in milliseconds in the range of [200..65535] for ESR-1000/1200/1500/1511 By default:
|
13 | Set the amount of dropped packets, at which the BFD neighbor is considered to be unavailable. (optional) | esr(config-if-gi)# ip bfd multiplier <COUNT> | <COUNT> – amount of dropped packets, at which the neighbor is considered to be unavailable, takes values in the range of [1..100]. Default: 5 |
14 | Switch BFD session to the passive mode, so that BFD messages will not be sent until the messages from BFD neighbor are received. On the interface | esr(config-if-gi)# ip bfd passive |
Configuration example of BFD with BGP
Objective:
Configure eBGP between ESR R1 and R2 and enable BFD.

Solution:
R1 configuration
Preconfigure Gi1/0/1 interface:esr(config)# interface gigabitethernet 1/0/1 esr(config-if-gi)# ip firewall disable esr(config-if-gi)# ip address 10.0.0.1/24CODEConfigure eBGP with BFD:
esr(config)# router bgp 100 esr(config-bgp)# address-family ipv4 esr(config-bgp-af)# neighbor 10.0.0.2 esr(config-bgp-neighbor)# remote-as 200 esr(config-bgp-neighbor)# update-source 10.0.0.1 esr(config-bgp-neighbor)# bfd-enable esr(config-bgp-neighbor)# enable esr(config-bgp-neighbor)# ex esr(config-bgp-af)# enable esr(config-bgp-af)# exitCODE- R2 configuration
Preconfigure Gi1/0/1 interface:
esr(config)# interface gigabitethernet 1/0/1 esr(config-if-gi)# ip firewall disable esr(config-if-gi)# ip address 10.0.0.2/24CODEConfigure eBGP with BFD:
esr(config)# router bgp 200 esr(config-bgp)# address-family ipv4 esr(config-bgp-af)# neighbor 10.0.0.1 esr(config-bgp-neighbor)# remote-as 100 esr(config-bgp-neighbor)# update-source 10.0.0.2 esr(config-bgp-neighbor)# bfd-enable esr(config-bgp-neighbor)# enable esr(config-bgp-neighbor)# ex esr(config-bgp-af)# enable esr(config-bgp-af)# exitCODE
PBR routing policy configuration
Configuration algorithm of Route-map for BGP
Route-maps may serve as filters processing routing information when it is received from or sent to the neighbouring device. Processing may include filtering based on various route criteria and setting attributes (MED, AS-PATH, community, LocalPreference, etc.) for the respective routes.
Also, Route-map may assign routes based on access control lists (ACL).
Step | Description | Command | Keys |
|---|---|---|---|
1 | Create a route map for | esr(config)# route-map <NAME> | <NAME> – router map name, set by the string of up to 31 characters. |
2 | Create a route map rule. | esr(config-route-map)# rule <ORDER> | <ORDER> – rule number, takes values of [1..10000]. |
3 | Specify the action that should be applied for routing information. | esr(config-route-map-rule)# action <ACT> | <ACT> – allocated action:
|
4 | Set BGPAS-Path attribute value in the route for which the rule should work | esr(config-route-map-rule)# match as-path [begin | end | contain] <AS-PATH> | <AS-PATH> – list of stand alone system numbers, defined as AS,AS,AS, takes values of [1..4294967295]. Optional parameters:
|
5 | Set BGPCommunity attribute value for which the rule should work (optionally). | esr(config-route-map-rule)# match community <COMMUNITY-LIST> | <COMMUNITY-LIST> – community list, defined as AS:N,AS:N, takes values of [1..4294967295]. You can specify up to 64 community. |
6 | BGPExtendedCommunity attribute value for which the rule should work (optionally). | esr(config-route-map-rule)# match extcommunity <EXTCOMMUNITY-LIST> | <EXTCOMMUNITY-LIST> – extcommunity list, defined as KIND:AS:N, KIND:AS:N, where KIND – extcommunity type:
N – extcommunity number, takes values of [1..65535]. |
7 | Set IP addresses profile including destination subnet values in the route (optionally). | esr(config-route-map-rule)# match ip address object-group <OBJ-GROUP-NETWORK-NAME> | <OBJ-GROUP-NETWORK-NAME> – name of the IP addresses profile that includes destination subnets prefixes, set by the string of up to 31 characters. |
esr(config-route-map-rule)# match ipv6 address object-group <OBJ-GROUP-NETWORK-NAME> | |||
8 | Set IP addresses profile that includes BGPNext-Hop attribute value in the route for which the rule should work (optionally). | esr(config-route-map-rule)# match ip next-hop object-group <OBJ-GROUP-NETWORK-NAME> | <OBJ-GROUP-NETWORK-NAME> – name of the IP addresses profile that includes destination subnets prefixes, set by the string of up to 31 characters. |
esr(config-route-map-rule)# match ipv6 next-hop object-group <OBJ-GROUP-NETWORK-NAME> | |||
9 | Set the profile that includes IP addresses of the router having advertised the route for which the rule should work (optionally). | esr(config-route-map-rule)# match ip route-source object-group <OBJ-GROUP-NETWORK-NAME> | <OBJ-GROUP-NETWORK-NAME> – name of the IP addresses profile that includes destination subnets prefixes, set by the string of up to 31 characters. |
esr(config-route-map-rule)# match ipv6 route-source object-group <OBJ-GROUP-NETWORK-NAME> | |||
10 | Specify ACL group for which the rule should work. | esr(config-route-map-rule)# match access-group <NAME> | <NAME> – access control list name, set by the string of up to 31 characters. |
11 | Set BGP MED attribute value in the route for which the rule should work (optionally). | esr(config-route-map-rule)# match metric bgp <METRIC> | <METRIC> – BGP MED attribute value, takes values in the range of [0..4294967295]. |
12 | Set OSPF Metric attribute value in the route for which the rule should work. | esr(config-route-map-rule)# match metric ospf <TYPE> <METRIC> | <TYPE> – OSPF Metric attribute type, takes values type-1 and type-2; <METRIC> – OSPF Metric attribute value, takes values in the range of [0..65535]. |
13 | Set RIP Metric attribute value in the route for which the rule should work. | esr(config-route-map-rule)# match metric rip <METRIC> | <METRIC> – RIP Metric attribute value, takes values in the range of [0..16]. |
14 | Set OSPF Tag attribute value in the route for which the rule should work. | esr(config-route-map-rule)# match tag ospf <TAG> | <TAG> – OSPF Tag attribute value, takes values in the range of [0..4294967295]. |
15 | Set RIP Tag attribute value in the route for which the rule should work. | esr(config-route-map-rule)# match tag rip <TAG> | <RIP> – RIP Tag attribute value, takes values in the range of [0..65535]. |
16 | Set BGP AS-Path attribute value that will be added to the beginning of AS-Path list (optionally). | esr(config-route-map-rule)# action set as-path | <AS-PATH> – stand alone systems number list that will be added to the current value in the route. Set as AS, AS, AS, takes values of [1..4294967295]. <TCACK-ID> – vrrp-tracking identifier that provides the specified action execution. Changes in the range of [1..60]. |
17 | Set BGP Community attribute value that will be specified in the route (optionally). | esr(config-route-map-rule)# action set community {COMMUNITY-LIST> | no-advertise | no-export } | <COMMUNITY-LIST> – community list, defined as AS:N,AS:N, where each part takes values of [1..65535].
|
18 | Set BGP ExtCommunity attribute value that will be specified in the route (optionally). | esr(config-route-map-rule)# action set extcommunity <EXTCOMMUNITY-LIST> | <EXTCOMMUNITY-LIST> – extcommunity list, defined as KIND:AS:N, KIND:AS:N, where KIND – extcommunity type:
N – extcommunity number, takes values of [1..65535]. |
19 | Specify BGP Next-Hop attribute that will be set in the route when advertising (optionally). | esr(config-route-map-rule)# action set ip bgp-next-hop <ADDR> | <ADDR> – gateway IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
esr(config-route-map-rule)# action set ipv6 bgp-next-hop <IPV6-ADDR> | <IPV6-ADDR> – gateway IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]. | ||
20 | Specify Next-Hop value that will be set in the route received by BGP (optionally). | esr(config-route-map-rule)# action set ip next-hop {NEXTHOP> | blackhole | unreachable | prohibit} | <NEXTHOP> – gateway IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255];
|
esr(config-route-map-rule)# action set ipv6 next-hop <IPV6-NEXTHOP> | <IPV6-ADDR> – gateway IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]. | ||
21 | Specify BGP Local Preference attribute value that will be set in the route (optionally). | esr(config-route-map-rule)# action set local-preference <PREFERENCE> | <PREFERENCE> – BGP Local Preference attribute value, takes values in the range of [0..255]. |
22 | Specify BGP Origin attribute value that will be set in the route (optionally). | esr(config-route-map-rule)# action set origin <ORIGIN> | <ORIGIN> – BGP Origin attribute value:
|
23 | Specify BGP MED value that will be set in the route | esr(config-route-map-rule)# action set metric bgp <METRIC> | <METRIC> – BGP MED attribute value, takes values in the range of [0..4294967295]. |
24 | Add filtration and modification of routes in incoming or outgoing directions. | esr(config-bgp-neighbor)# route-map <NAME><DIRECTION> | <NAME> – name of the route map having been configured; <DIRECTION> – direction:
|
esr(config-ipv6-bgp-neighbor)# route-map <NAME><DIRECTION> |
Configuration example 1. Route-map for BGP
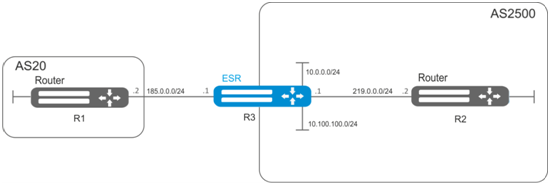
Objective:
Assign community for routing information coming from AS 20:
First, do the following:
- Configure BGP with AS 2500 on ESR router;
- Establish neighbouring with AS20.
Solution:
Create a policy:
esr# configure
esr(config)# route-map from-as20Create rule 1:
esr(config-route-map)# rule 1If AS PATH contains AS 20, assign community 20:2020 to it and exit:
esr(config-route-map-rule)# match as-path contain 20
esr(config-route-map-rule)# action set community 20:2020
esr(config-route-map-rule)# exit
esr(config-route-map)# exitIn AS 2500 BGP process, enter neighbour parameter configuration:
esr(config)# router bgp 2500
esr(config-bgp)# address-family ipv4
esr(config-bgp-af)# neighbor 185.0.0.2Map the policy to routing information:
esr(config-bgp-neighbor)# route-map from-as20 inConfiguration example 2. Route-map for BGP
Objective:
For the whole transmitted routing information (from community 2500:25), assign MED equal to 240 and define EGP routing information source:
First:
Configure BGP with AS 2500 on ESR
Solution:
Create a policy:
esr(config)# route-map to-as20Create rule:
esr(config-route-map)# rule 1If community contains 2500:25, assign MED 240 and Origin EGP to it:
esr(config-route-map-rule)# match community 2500:25
esr(config-route-map-rule)# action set metric bgp 240
esr(config-route-map-rule)# action set origin egp
esr(config-route-map-rule)# exit
esr(config-route-map)# exitIn AS 2500 BGP process, enter neighbour parameter configuration:
esr(config)# router bgp 2500
esr(config-bgp)# address-family ipv4
esr(config-bgp-af)# neighbor 185.0.0.2Map the policy to routing information being advertised:
esr(config-bgp-neighbor)# route-map to-as20 out
esr(config-bgp-neighbor)# exit
esr(config-bgp)# exit
esr(config)# exitRoute-map based on access control lists (Policy-based routing) configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Create a route map for IP routes filtration and modification. | esr(config)# route-map <NAME> | <NAME> – router map name, set by the string of up to 31 characters. |
2 | Create a route map rule | esr(c onfig-route-map)# rule <ORDER> | <ORDER> – rule number, takes values of [1..10000]. |
3 | Specify the action that should be applied for routing information. | esr(config-route-map-rule)# action <ACT> | <ACT> – allocated action:
|
4 | Set ACL for which the rule should work (optionally). | esr(config-route-map-rule)# match ip access-group <NAME> | <NAME> – access control list name, set by the string of up to 31 characters. |
5 | Set Next-Hop for the packets that meet the requirements of the specified ACL (optionally). | esr(config-route-map-rule)# action set ip next-hop verify-availability <NEXTHOP><METRIC> | <NEXTHOP> – gateway IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]; <METRIC> – route metric, takes values of [0..255]. |
6 | Specify ACL-based routing policy. | esr(config-if-gi)# ip policy route-map <NAME> | <NAME> – configured routing policy name, set by the string of up to 31 characters. |
Route-map based on access control lists (Policy-based routing) configuration example
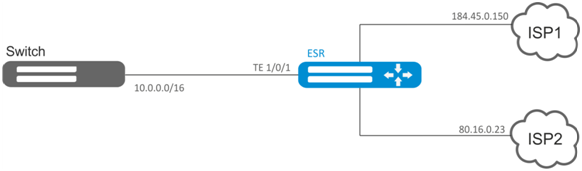
Objective:
Distribute traffic between Internet service providers based on user subnets.
First, assign IP address to interfaces.
Route traffic from addresses 10.0.20.0/24 through ISP1 (184.45.0.150), and traffic from addresses 10.0.30.0/24 – through ISP2 (80.16.0.23). You should monitor availability of ISP addresses (ISP connection operational capability), and if one the connections goes down, redirect all the traffic from malfunctioning connection to the operational one.
Solution:
Create ACL:
esr# configure
esr(config)# ip access-list extended sub20
esr(config-acl)# rule 1
esr(config-acl-rule)# match source-address 10.0.20.0 255.255.255.0
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# match protocol any
esr(config-acl-rule)# action permit
esr(config-acl-rule)# enable
esr(config-acl-rule)# exit
esr(config-acl)# exit
esr(config)# ip access-list extended sub30
esr(config-acl)# rule 1
esr(config-acl-rule)# match source-address 10.0.30.0 255.255.255.0
esr(config-acl-rule)# match destination-address any
esr(config-acl-rule)# match protocol any
esr(config-acl-rule)# action permit
esr(config-acl-rule)# enable
esr(config-acl-rule)# exit
esr(config-acl)# exitCreate a policy:
esr(config)# route-map PBRCreate rule 1:
esr(config-route-map)# rule 1Specify ACL as a filter:
esr(config-route-map-rule)# match ip access-group sub20Specify next-hop for sub20:
esr(config-route-map-rule)# action set ip next-hop verify-availability 184.45.0.150 10
esr(config-route-map-rule)# action set ip next-hop verify-availability 80.16.0.23 30
esr(config-route-map-rule)# exit
esr(config-route-map)# exitRule 1 should provide traffic routing from the network 10.0.20.0/24 to address 184.45.0.150, and in case of its failure, to address 80.16.0.23. Gateway precedence is defined by metrics values – 10 and 30.
Create rule 2:
esr(config-route-map)# rule 2Specify ACL as a filter:
esr(config-route-map-rule)# match ip access-group sub30Specify nexthop for sub30 and exit:
esr(config-route-map-rule)# action set ip next-hop verify-availability 80.16.0.23 10
esr(config-route-map-rule)# action set ip next-hop verify-availability 184.45.0.150 30
esr(config-route-map-rule)# exit
esr(config-route-map)# exitRule 2 should provide traffic routing from the network 10.0.30.0/24 to address 80.16.0.23, and in case of its failure, to address 184.45.0.150. Precedence is defined by metrics values.
Switch to TE 1/0/1 interface:
esr(config)# interface tengigabitethernet 1/0/1Map the policy the respective interface:
esr(config-if-te)# ip policy route-map PBRVRF Lite configuration
VRF (Virtual Routing and Forwarding) is a technology designed for isolation of routing information that belongs to different classes (e.g., routes of a specific client).
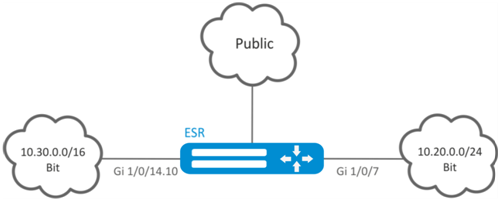
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Create VRF instance and switch to the VRF instance parameters configuration mode. | esr(config)# ip vrf <VRF> | <VRF> – VRF instance name, set by the string of up to 31 characters. |
2 | Assign the description of the configured VRF instance. | esr(config-vrf)# description <DESCRIPTION> | <DESCRIPTION> – VRF instance description, set by the string of up to 255 characters. |
3 | Set the capacity of routing tables in configured VRF for IPv4/IPv6 (optionally). | esr(config-vrf)# ip protocols <PROTOCOL> max-routes <VALUE> | <PROTOCOL> – protocol type, takes the following values: ospf, bgp; <VALUE> – amount of routes in the routing table, takes values in the range of:
Default value: 0 |
esr(config-vrf)#ipv6 protocols <PROTOCOL> max-routes <VALUE> | |||
4 | Enable and configure dynamic traffic routing protocols (Static/OSPF/BGP/IS-IS) in VRF instance (optional). See the related sections: Static routes configuration, OSPF configuration, and BGP configuration. | ||
5 | In the configuration mode of physical/logical interface, tunnel, DNAT/SNAT rule, DAS server or SNMPv3 user, specify the name of VRF instance for which the mode will be used (optionally). | esr(config-snat-ruleset)# ip vrf forwarding <VRF> | <VRF> – VRF instance name, set by the string of up to 31 characters. |
6 | Configure LT tunnel to transmit traffic to global mode or to other VRFs (if required). |
| See section LT tunnel configuration |
Configuration example
Objective:
ESR series router features 2 connected networks that should be isolated from other networks.
Solution:
Create VRF:
esr(config)# ip vrf bit
esr(config-vrf)# exitCreate a security zone:
esr(config)# security zone vrf-sec
esr(config-zone)# ip vrf forwarding bit
esr(config-zone)# exitCreate rule for a pair of zones and allow all TCP/UDP traffic:
esr(config)# security zone-pair vrf-sec vrf-sec
esr(config-zone-pair)# rule 1
esr(config-zone-rule)# match source-address any
esr(config-zone-rule)# match destination-address any
esr(config-zone-rule)# match protocol udp
esr(config-zone-rule)# match source-port any
esr(config-zone-rule)# match destination-port any
esr(config-zone-rule)# action permit
esr(config-zone-rule)# enable
esr(config-zone-rule)# exit
esr(config-zone-pair)# rule 2
esr(config-zone-rule)# match source-address any
esr(config-zone-rule)# match destination-address any
esr(config-zone-rule)# match protocol tcp
esr(config-zone-rule)# match source-port any
esr(config-zone-rule)# match destination-port any
esr(config-zone-rule)# action permit
esr(config-zone-rule)# enable
esr(config-zone-rule)# exitCreate interface mapping, assign IP addresses, specify an inherence to a security zone:
esr(config)# interface gigabitethernet 1/0/7
esr(config-if-gi)# ip vrf forwarding bit
esr(config-if-gi)# ip address 10.20.0.1/24
esr(config-if-gi)# security-zone vrf-sec
esr(config-if-gi)# exit
esr(config)# interface gigabitethernet 1/0/14.10
esr(config-subif)# ip vrf forwarding bit
esr(config-subif)# ip address 10.30.0.1/16
esr(config-subif)# security-zone vrf-sec
esr(config-subif)# exit
esr(config)# exitTo view information on interfaces mapped to VRF, use the following command:
esr# show ip vrf To view VRF routing table, use the following command:
esr# show ip route vrf bitMultiWAN configuration
MultiWAN technology establishes a fail-safe connection with redundancy of links from multiple providers and solves the problem involving traffic balancing between redundant links.
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Configure interfaces through which MultiWAN will operate: set IP addresses and specify security zone. | ||
2 | Write static routes through WAN (if required). | esr(config)# ip route <SUBNET> wan load-balance rule <ID> [<METRIC>] | <ID> – identifier of the rule being created (see item 2). <METRIC> – route metric, takes values of [0..255]. |
3 | Create WAN rule and switch to the rule parameters configuration mode. | esr(config)# wan load-balance rule <ID> | <ID> – identifier of the rule being created, takes values in the range of [1..50]. |
4 | Specify interfaces or tunnels which are gateways in the route created by MultiWAN service. | esr(config-wan-rule)# outbound | <IF>– interface name; <TUN> – tunnel name; [WEIGHT] – tunnel or interface weight, defined in the range of [1..255]. If the value is equal 2, than 2 times more traffic will be transmit via the given interface than via the interface with the default value. A route with the highest weight will be active in the redundancy mode. Default value: 1 |
5 | Describe the rules (optionally). | esr(config-wan-rule)# description <DESCRIPTION> | <DESCRIPTION> – wan rule description, set by the string of up to 255 characters. |
6 | You can use this command to switch from the balancing mode to the redundancy mode. | esr(config-wan-rule)# failover | |
7 | Enable wan rule. | esr(config-wan-rule)# enable | |
8 | Create a list of IP addresses to check the connection integrity and perform the switching to the list parameters configuration mode. | esr(config)# wan load-balance target-list <NAME> | <NAME> – list name, set by the string of up to 31 characters. |
9 | Specify the check target and switch to the target parameters configuration mode. | esr(config-target-list)# target <ID> | <ID> – target identifier, set in the range of [1..50]. If the “all” parameter value is used when removing, all targets for the configured target list will be removed. |
10 | Describe target (optionally). | esr(config-wan-target)# description <DESCRIPTION> | <DESCRIPTION> – target description, set by the string of up to 255 characters. |
11 | Specify the standby time via ICMP (optionally). | esr(config-wan-target)# resp-time <TIME> | <TIME> – timeout, takes value in seconds [1..30]. |
12 | Specify IP address of the check. | esr(config-wan-target)# ip address <ADDR> | <ADDR> – destination IP address, defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. |
esr(config-wan-target)# ipv6 address <IPV6-ADDR> | <IPV6-ADDR> – destination IPv6 address, defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]. | ||
13 | Enable the target check. | esr(config-wan-target)# enable | |
Commands for 14-17 items should be applied on interfaces/tunnels in MultiWAN | |||
14 | Enable WAN mode on the interface for IPv4/IPv6 stack. | esr(config-if-gi)# wan load-balance enable | |
esr(config-if-gi)# ipv6 wan load-balance enable | |||
15 | Set the amount of ineffective attempts to check the connection, after which, if there is not response from the opposing side, the connection is considered to be inactive (optionally). | esr(config-if-gi)# wan load-balance failure-count <VALUE> | <VALUE> – number of attempts, takes values in the range of [1..10]. Default value: 1 |
esr(config-if-gi)# ipv6 wan load-balance failure-count <VALUE> | |||
16 | Set the amount of successful attempts to check the connection, after which, if successful, the connection is considered to be active again (optional). | esr(config-if-gi)# wan load-balance success-count <VALUE> | <VALUE> – number of attempts, takes values in the range of [1..10]. Default value: 1 |
esr(config-if-gi)# ipv6 wan load-balance success-count <VALUE> | |||
17 | Set a neighbour's IP address that will be indicated as one of the gateways in a static route created by MultiWAN service. | esr(config-if-gi)# wan load-balance nexthop { <IP> | dhcp enable | tunnel enable } | <IP> – destination IP address (gateway), defined as AAA.BBB.CCC.DDD where each part takes values of [0..255]. dhcp enable – if on the interface an IP address is obtained through a DHCP client, the gateway from the DHCP server is used. tunnel enable – use as nexthop – destination p-t-p address. Applicable for the interfaced being connected that operate via ppp. |
esr(config-if-gi)# ipv6 wan load-balance nexthop { <IPV6> } | <IPV6> – destination IPv6 address (gateway), defined as X:X:X:X::X where each part takes values in hexadecimal format [0..FFFF]. | ||
18 | This command will be checking the IP addresses from the integrity check list. If all (default)/at least one (using the chack-all key) of the tested hosts is unavailable, the gateway is considered unavailable. | esr(config-if-gi)# wan load-balance target-list { check-all | <NAME> } | <NAME> – run check on the basis of a certain target list (specified in item 7). check-all – run check on the basis of all targets in the list. |
esr(config-if-gi)# ipv6 wan load-balance target-list { check-all | <NAME> } | |||
19 | Write static routes through WAN. | esr(config)# ip route <SUBNET> wan load-balance rule <ID> [<METRIC>] | <ID> – identifier of the rule being created (see item 2). <METRIC> – route metric, takes values of [0..255]. |
esr(config)# ipv6 route <SUBNET> wan load-balance rule <ID [<METRIC>] | |||
Configuration example
Objective:
Configure route to the server (108.16.0.1/28) with the load balancing option.
Solution:
First, do the following:
- Configure zones for te1/0/1 and te1/0/2 interfaces.
- Specify IP addresses for te1/0/1 and te1/0/2 interfaces.
Main configuration step:
Configure routing:
esr(config)# ip route 108.16.0.0/28 wan load-balance rule 1Create WAN rule:
еsr(config)# wan load-balance rule 1Specify affected interfaces:
еsr(config-wan-rule)# outbound interface tengigabitethernet 1/0/2
еsr(config-wan-rule)# outbound interface tengigabitethernet 1/0/1Enable the created balancing rule and exit the rule configuration mode:
еsr(config-wan-rule)# enable
еsr(config-wan-rule)# exitCreate a list for the connection integrity check:
еsr(config)# wan load-balance target-list googleCreate integrity check target:
esr(config-target-list)# target 1 Specify address to be checked, enable check for the specified address and exit:
еsr(config-wan-target)# ip address 8.8.8.8
еsr(config-wan-target)# enable
еsr(config-wan-target)# exitConfigure interfaces. In te1/0/1 interface configuration mode, specify nexthop:
еsr(config)# interface tengigabitethernet 1/0/1
еsr(config-if)# wan load-balance nexthop 203.0.0.1In te1/0/1 interface configuration mode, specify a list of targets for connection check:
еsr(config-if)# wan load-balance target-list googleIn te1/0/1 interface configuration mode, enable WAN mode and exit:
еsr(config-if)# wan load-balance enable
еsr(config-if)# exitIn te1/0/2 interface configuration mode, specify nexthop:
еsr(config)# interface tengigabitethernet 1/0/2
еsr(config-if)# wan load-balance nexthop 65.6.0.1In te1/0/2 interface configuration mode, specify a list of targets for connection check:
еsr(config-if)# wan load-balance target-list googleIn te1/0/2 interface configuration mode, enable WAN mode and exit:
еsr(config-if)# wan load-balance enable
еsr(config-if)# exitTo switch into redundancy mode, configure the following:
Proceed to WAN rule configuration mode:
еsr(config)# wan load-balance rule 1MultiWAN function may also work in redundancy mode when traffic is directed to the active interface with the highest weight. To enable this mode, use the following command:
еsr(config-wan-rule)# failoverIS-IS configuration
IS-IS — ISO standardized dynamic routing protocol based on link-state. It provides fast convergence and excellent scalability, makes economical use of network bandwidth, and uses the Dijkstra Algorithm to calculate the best routes. A distinctive feature of the IS-IS protocol is to work on top of the data link layer of the OSI model, so it is not binded to a specific network layer protocol.
Configuration algorithm
Step | Description | Command | Keys |
|---|---|---|---|
1 | Create an IS-IS process and switch to the parameters configuration mode of this process. | esr(config)# router isis <ID> [vrf <VRF>] | <ID> – process number, takes values of [1..65535]; <VRF> – VRF instance name, set by the string of up to 31 characters. |
2 | Set NET address. | esr(config-isis)# net {<NET>} | <NET> – NET address, format: ff[.ffff.ffff.ffff.ffff.ffff.ffff].ffff.ffff.ffff.00. |
3 | Enable IS-IS process. | esr(config-isis)# enable | |
4 | Set the authentication algorithm for the L2 layer (optional). | esr(config-isis)# authentication domain algorithm <ALGORITHM> | <ALGORITHM> – authentication algorithm:
|
5 | Set the authentication password for the L2 layer (optional). | esr(config-isis)# authentication domain key ascii-text { <CLEAR-TEXT> | encrypted <ENCRYPTED-TEXT> } | <CLEAR-TEXT> – password, set by the string of 8 characters; <ENCRYPTED-TEXT> – encrypted password of 8 bytes (16 characters) in hexadecimal format (0xYYYY ...) or (YYYY ...). |
6 | Set a list of keys for authentication (optional). | esr(config-isis)# authentication domain key chain <KEYCHAIN> | <KEYCHAIN> – key list identifier, set by the string of up to 16 characters. |
7 | Select the authentication algorithm for the L1 layer (optional). | esr(config-isis)# authentication area algorithm <ALGORITHM> | <ALGORITHM> – authentication algorithm:
|
8 | Set the authentication password for the L1 layer (optional). | esr(config-isis)# authentication area key ascii-text { <CLEAR-TEXT> | encrypted <ENCRYPTED-TEXT> } | <CLEAR-TEXT> – password, set by the string of 8 characters; <ENCRYPTED-TEXT> – encrypted password of 8 bytes (16 characters) in hexadecimal format (0xYYYY ...) or (YYYY ...). |
9 | Set a list of keys for authentication (optional). | esr(config-isis)# authentication area key chain <KEYCHAIN> | <KEYCHAIN> – key list identifier, set by the string of up to 16 characters. |
10 | Enable transmission of router name to the LSP (optional). | esr(config-isis)# hostname dynamic | |
11 | Set the IS-IS process operating level (optional). | esr(config-isis)# is-type {<LEVEL>} | <LEVEL> – IS-IS protocol operation level:
|
12 | Set the type of metric to be used in the IS-IS process (optional). | esr(config-isis)# metric-style { narrow | wide | transition } [<LEVEL>] | narrow — accepts and generates TLVs (on network reachability) of the old type; wide — accepts and generates TLVs (on network reachability) of the new type; transition — accepts and generates TLVs (on network reachability) of the new and old type; <LEVEL> – IS-IS protocol operation level:
|
13 | Set the route priority for the specified IS-IS process (optional). | esr(config-isis)# preference {<VALUE>} | <VALUE> – may take values [1..255]. |
14 | Enable IS-IS operation with IPv4 and/or IPv6 addresses (optional). | esr(config-isis)# address-family { ipv4 | ipv6 } | ipv4 – IPv4 family; ipv6 – IPv6 family. |
15 | Set the update interval for own LSP (optional). | esr(config-isis)# lsp-refresh-interval { min | max } <TIME> [ <LEVEL> ] | min — minimum update/generation interval; max — maximum update/generation interval; <TIME> – time in seconds, takes values of [1..65535]; <LEVEL> – IS-IS protocol operation level:
|
16 | Set the lifetime of own LSP (optional). | esr(config-isis)# max-lsp-lifetime <TIME> [<LEVEL>] | <TIME> – time in seconds, takes values of [1..65535]; <LEVEL> – IS-IS protocol operation level:
|
17 | Set a timeout before the next SPF calculation (optional). | esr(config-isis)# spf-timeout <TIME> [<LEVEL>] | <TIME> – time in milliseconds, takes values of [1..10000]; <LEVEL> – IS-IS protocol operation level:
|
18 | Enable advertising of routes received in an alternative way (optionally). | esr(config-isis)# redistribute bgp <AS> [ route-map <NAME> ] [is-type <LEVEL>] | <AS> – stand alone system number, takes values of [1..4294967295]. <NAME> – name of the route map that will be used for advertised routes filtration and modification, set by the string of up to 31 characters; <LEVEL> – IS-IS protocol operation level:
|
esr(config-isis)# redistribute ipv6 bgp <AS> [ route-map <NAME> ] [is-type <LEVEL>] | |||
esr(config-isis)# redistribute ospf <ID> <ROUTE-TYPE> [ route-map <NAME> ] [is-type <LEVEL>] | <ID> – process number, takes values of [1..65535]. <ROUTE-TYPE> – route type:
<NAME> – name of the route map that will be used for advertised OSFP routes filtration and modification, set by the string of up to 31 characters; <LEVEL> – IS-IS protocol operation level:
| ||
esr(config-isis)# redistribute ipv6 ospf <ID> <ROUTE-TYPE> [ route-map <NAME> ] [is-type <LEVEL>] | |||
esr(config-isis)# redistribute isis <ID> <ROUTE-TYPE> [ route-map <NAME> ] [is-type <LEVEL>] | <ID> – process number, takes values of [1..65535]. <ROUTE-TYPE> – route type:
<NAME> – name of the route map that will be used for advertised IS-IS routes filtration and modification, set by the string of up to 31 characters; <LEVEL> – IS-IS protocol operation level:
| ||
esr(config-isis)# redistribute rip [ route-map <NAME> ] [is-type <LEVEL>] | <NAME> – name of the route map that will be used for advertised RIP routes filtration and modification, set by the string of up to 31 characters; <LEVEL> – IS-IS protocol operation level:
| ||
esr(config-isis)# redistribute static [ route-map <NAME> ] [is-type <LEVEL>] | <NAME> – name of the route map that will be used for advertised static routes filtration and modification, set by the string of up to 31 characters; <LEVEL> – IS-IS protocol operation level:
| ||
esr(config-isis)# redistribute connected [ route-map <NAME> ] [is-type <LEVEL>] | <NAME> – name of the route map that will be used for advertised connected routes filtration and modification, set by the string of up to 31 characters; <LEVEL> – IS-IS protocol operation level:
| ||
19 | Add subnets filtration in incoming or outgoing updates (optionally). | esr(config-isis)# prefix-list { ipv6 <LIST_NAME> | <LIST_NAME> } {in|out} | <LIST-NAME> – name of a subnet list being configured, set by the string of up to 31 characters. in – incoming routes filtration; out – advertised routes filtration. |
20 | Add subnets filtration in incoming or outgoing updates (optionally). | esr(config-isis)# route-map <NAME> {in|out} | <NAME> – name of the route map that will be used for advertised routes filtration and modification, set by the string of up to 31 characters. |
21 | Set a matching of interface to a specified IS-IS process. | esr(config-if-gi)# isis instance <ID> | <ID> – process number, takes values of [1..65535]. |
22 | Enable the IS-IS protocol on the interface. | esr(config-if-gi)# isis enable | |
23 | Enable the use of TLV#8 in hello packets (optional). | esr(config-if-gi)# isis hello-padding | |
24 | Set the priority when selecting DIS (optional). | esr(config-if-gi)# isis priority <VALUE> [<LEVEL>] | <VALUE> – number, may take values [0..127]; <LEVEL> – IS-IS protocol operation level:
|
25 | Set the metric value for the interface (optional). | esr(config-if-gi)# isis metric <VALUE> [<LEVEL>] | <VALUE> – number, may take values [1..16777215]; <LEVEL> – IS-IS protocol operation level:
|
26 | Set defines which routing layer on the interface the current IS-IS process will run on (optional). | esr(config-if-gi)# isis circuit-type {<LEVEL>} | <LEVEL> – IS-IS protocol operation level:
|
27 | Set the interval for sending hello packets (optional). | esr(config-if-gi)# isis hello-interval <TIME> [<LEVEL>] | <TIME> – time in seconds, takes values of [1..65535]; <LEVEL> – IS-IS protocol operation level:
|
28 | Set the multiplier for calculating and sending Hold Time (optional). | esr(config-if-gi)# isis hello-multiplier <VALUE> [<LEVEL>] | <VALUE> – number, may take values [3..1000]; <LEVEL> – IS-IS protocol operation level:
|
29 | Set the interface to point-to-point IS-IS protocol mode (optional). | esr(config-if-gi)# isis network point-to-point | |
30 | Set the interval for generating and sending CSNP (optional). | esr(config-if-gi)# isis csnp-interval <TIME> [<LEVEL>] | <TIME> – time in seconds, takes values of [1..65535]; <LEVEL> – IS-IS protocol operation level:
|
31 | Set the interval for generating and sending PSNP (optional). | esr(config-if-gi)# isis psnp-interval <TIME> [<LEVEL>] | <TIME> – time in seconds, takes values of [1..65535]; <LEVEL> – IS-IS protocol operation level:
|
32 | Set the interval between LSP transmissions on the Broadcast network (optional). | esr(config-if-gi)# isis lsp-interval <TIME> [<LEVEL>] | <TIME> – time in milliseconds, takes values of [1-10000]; <LEVEL> – IS-IS protocol operation level:
|
33 | Set the LSP re-distribution interval in the PtP network (optional). | esr(config-if-gi)# isis lsp-retransmit-interval <TIME> [<LEVEL>] | <TIME> – time in seconds, takes values of [1..65535]; <LEVEL> – IS-IS protocol operation level:
|
34 | Set the authentication algorithm for the hello packets (optional). | esr(config-if-gi)# isis authentication algorithm <ALGORITHM> [<LEVEL>] | <ALGORITHM> – authentication algorithm:
<LEVEL> – IS-IS protocol operation level:
|
35 | Set the password for hello packet authentication (optionally). | esr(config-if-gi)# isis authentication key ascii-text { <CLEAR-TEXT> | encrypted <ENCRYPTED-TEXT> } [<LEVEL>] | <CLEAR-TEXT> – password, set by the string of 8 characters; <ENCRYPTED-TEXT> – encrypted password of 8 bytes (16 characters) in hexadecimal format (0xYYYY ...) or (YYYY ...); <LEVEL> – IS-IS protocol operation level:
|
36 | Set the key list for hello packet authentication (optionally). | esr(config-if-gi)# isis authentication key chain <KEYCHAIN> [<LEVEL>] | <KEYCHAIN> – key list identifier, set by the string of up to 16 characters; <LEVEL> – IS-IS protocol operation level:
|
Configuration example
Objective:
Configure the IS-IS protocol on routers to exchange routing information with neighbors. Router ESR1 will be L1-only, ESR2 will be L1/L2, ESR3 will be L2-only, which will also be in another area.
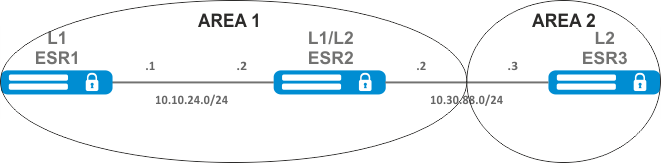
Solution:
Pre-configure IP addresses on interfaces according to the network structure shown in figure.
Proceed to the ESR1 router configuration. Create IS-IS process with identifier 1 and proceed to the protocol configuration mode:
ESR1(config)# router isis 1Set the number of the zone in which the router will operate and its system ID:
ESR1(config-isis)# net 49.0001.1111.1111.1111.00Configure the router to operate only on the first layer of the IS-IS protocol:
ESR1(config-isis)# is-type level-1Set the operation of the router with a narrow metric on the first level:
ESR1(config-isis)# metric-style narrow level-1Enable the IS-IS process on the router:
ESR1(config-isis)# enableProceed to the interface configuration. It is necessary to set the number of the IS-IS process which will run on the interface and to enable the protocol itself to run on it:
ESR1(config-if-gi)# isis instance 1
ESR1(config-if-gi)# isis enableProceed to the ESR2 router configuration.
ESR2(config)# router isis 2Set the zone number, the same as on ESR1, as well as a unique system identifier:
ESR2(config-isis)# net 49.0001.2222.2222.2222.00Set the router to operate with a narrow metric on the first layer and with a wide metric on the second layer, and enable this IS-IS process:
ESR2(config-isis)# metric-style narrow level-1
ESR2(config-isis)# metric-style wide level-2
ESR2(config-isis)# enable
Configure the interfaces on the router. The configuration will be the same on both interfaces.
ESR2(config-if-gi)# isis instance 2
ESR2(config-if-gi)# isis enable
Proceed to the ESR3 router configuration.
ESR3(config)# router isis 3
ESR3(config-isis)# net 49.0002.3333.3333.3333.00
ESR3(config-isis)# is-type level-2
ESR3(config-isis)# metric-style wide level-2
ESR3(config-isis)# enable
ESR3(config-if-gi)# isis instance 3
ESR3(config-if-gi)# isis enableThe neighborhood establishment can be viewed with the show isis neighbors command. Execute it on ESR2:
ESR2# show isis neighbors
IS-IS 2
IS-IS Level 1 Neighbors
System ID Hostname Interface State Holdtime SNPA
1111.1111.1111 ESR1 gi1/0/2 Up 25 a8f9.4baa.1d42
IS-IS Level 2 Neighbors
System ID Hostname Interface State Holdtime SNPA
3333.3333.3333 ESR3 gi1/0/1 Up 8 a8f9.4bab.813a